Introduction to privacy enhancing technologies (PET)
Figure 1
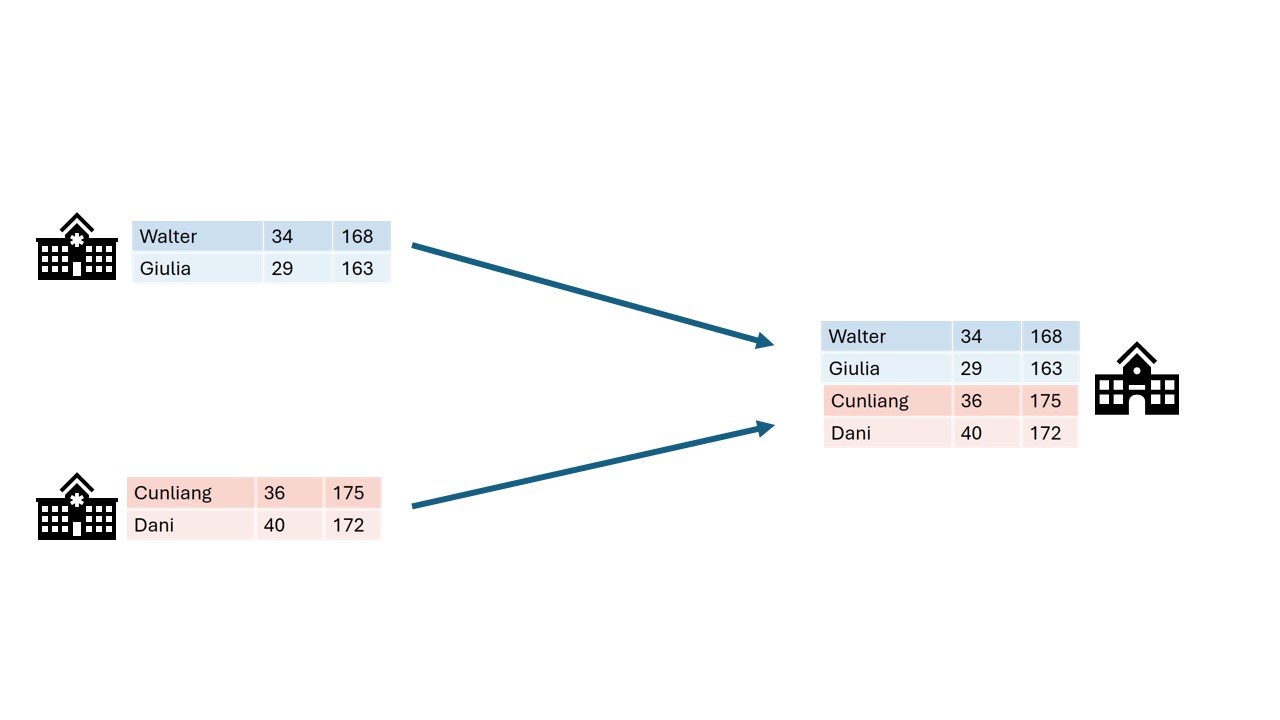
In classic analysis all the data is brought
together
Figure 2
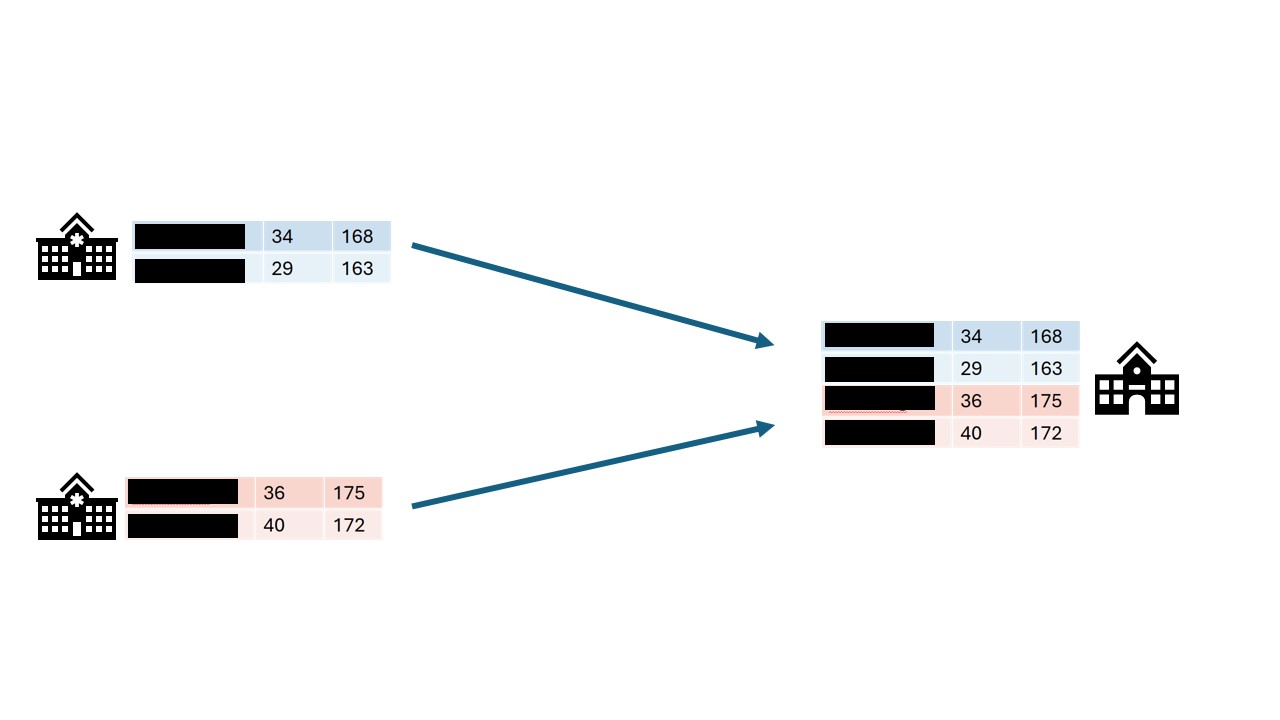
Data anonymization
Figure 3
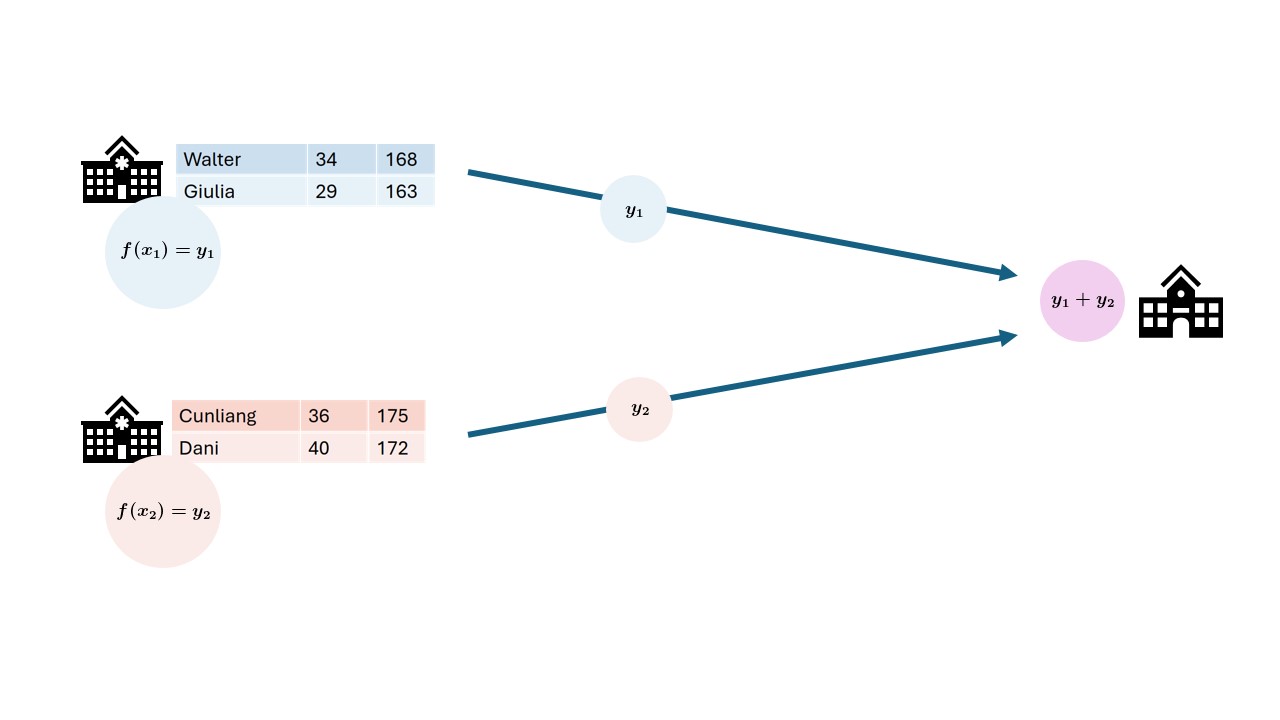
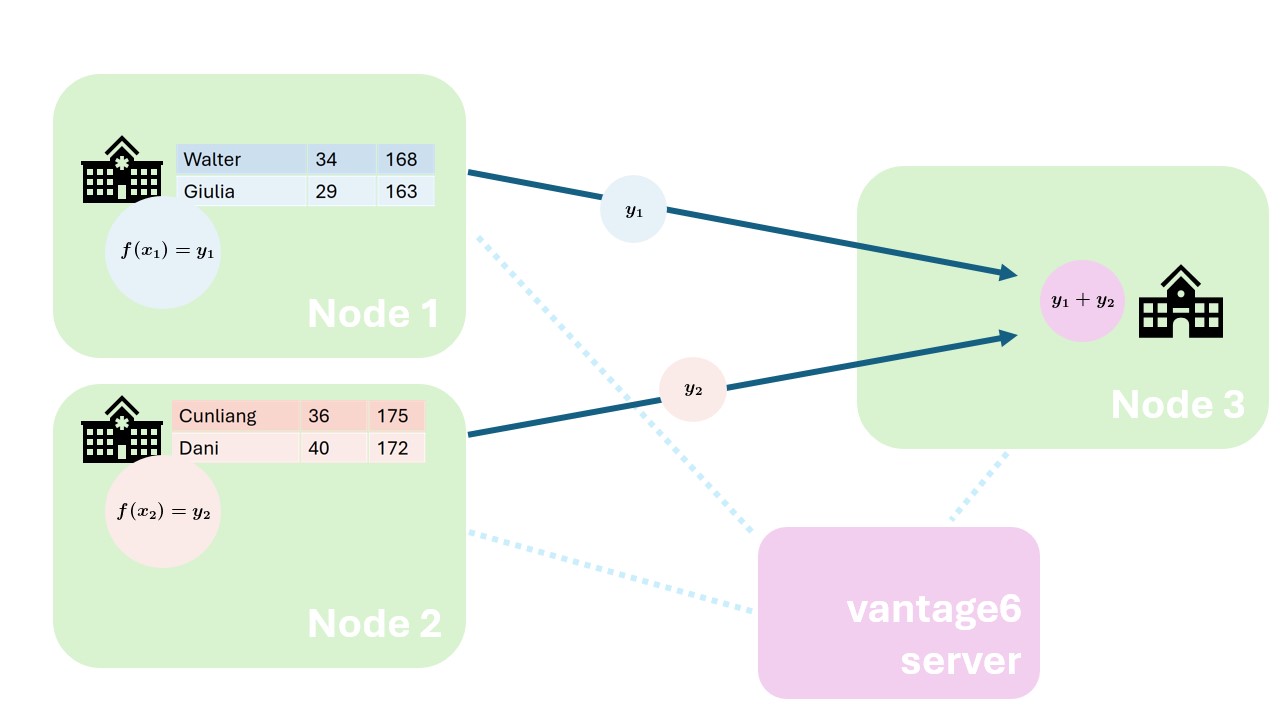
In federated analysis, an aggregation of the
local data is sent to a central point. At the central point the local
aggregations are combined. This can also be a small step in a larger
analysis.
Figure 4
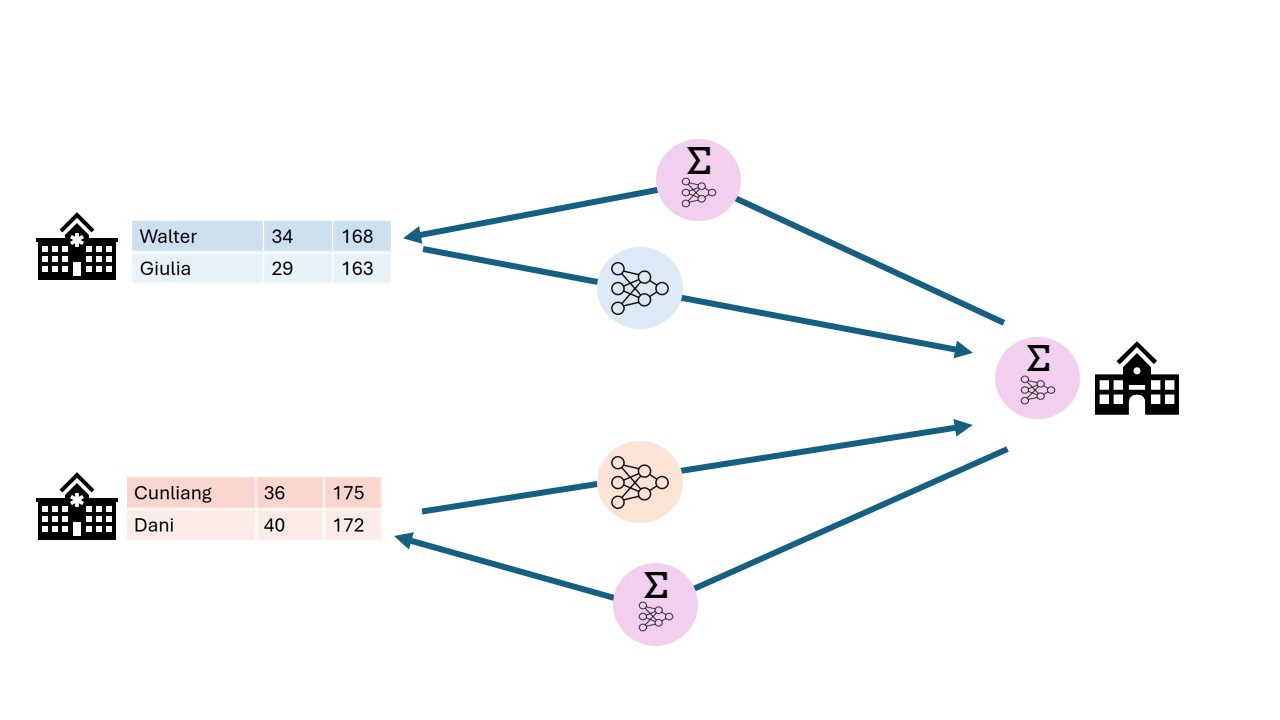
In federated learning only the gradients of
models are shared
Figure 5

An example of gradient leakage. The order might
not be correct but the images are still very close to the
originals.
Figure 6
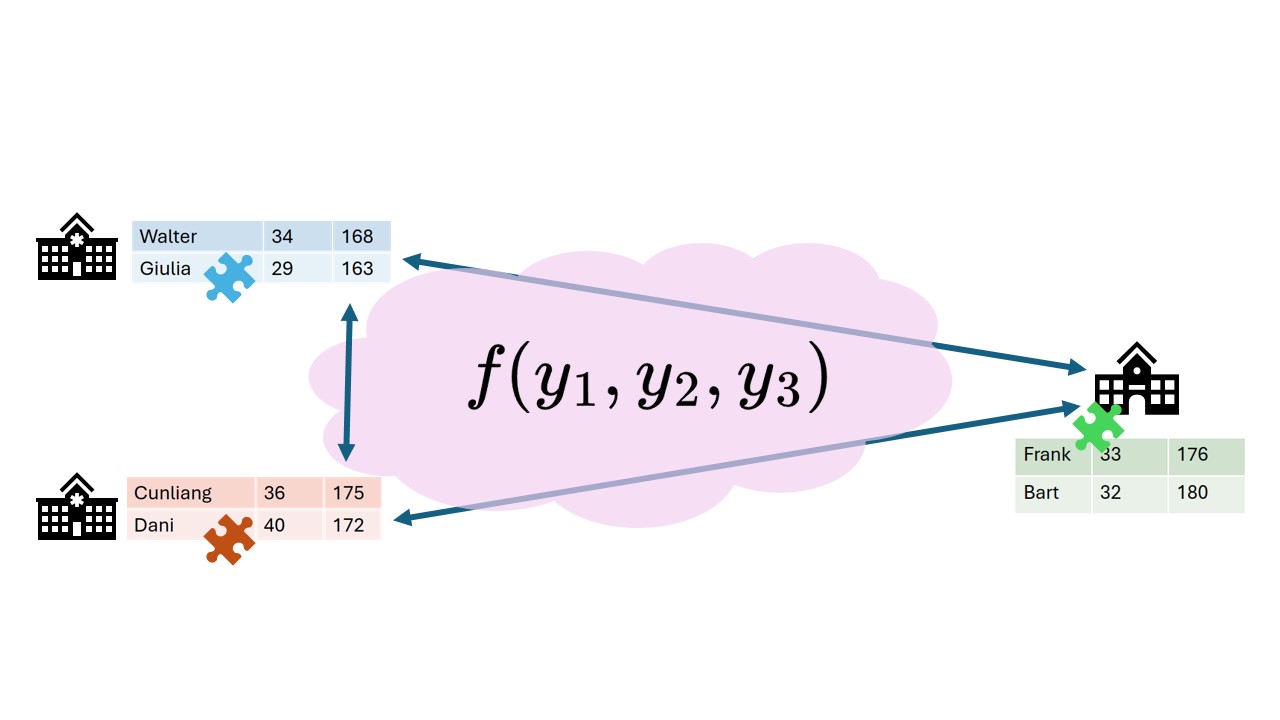
In secure multiparty computation parties
collaboratively perform an analysis while holding only encrypted pieces
of the data
Figure 7
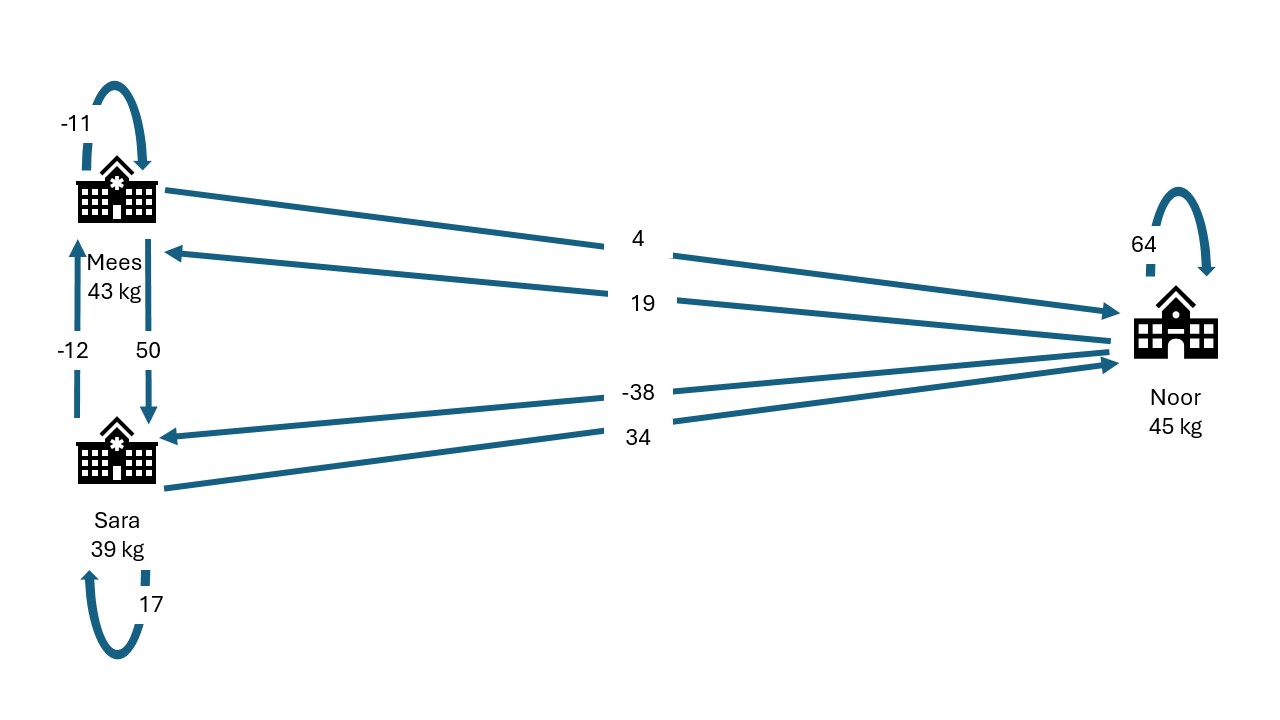
Mees, Sara and Noor distibute their secret
shares
Figure 8

Mees, Sara and Noor sum their secret
shares
Figure 9
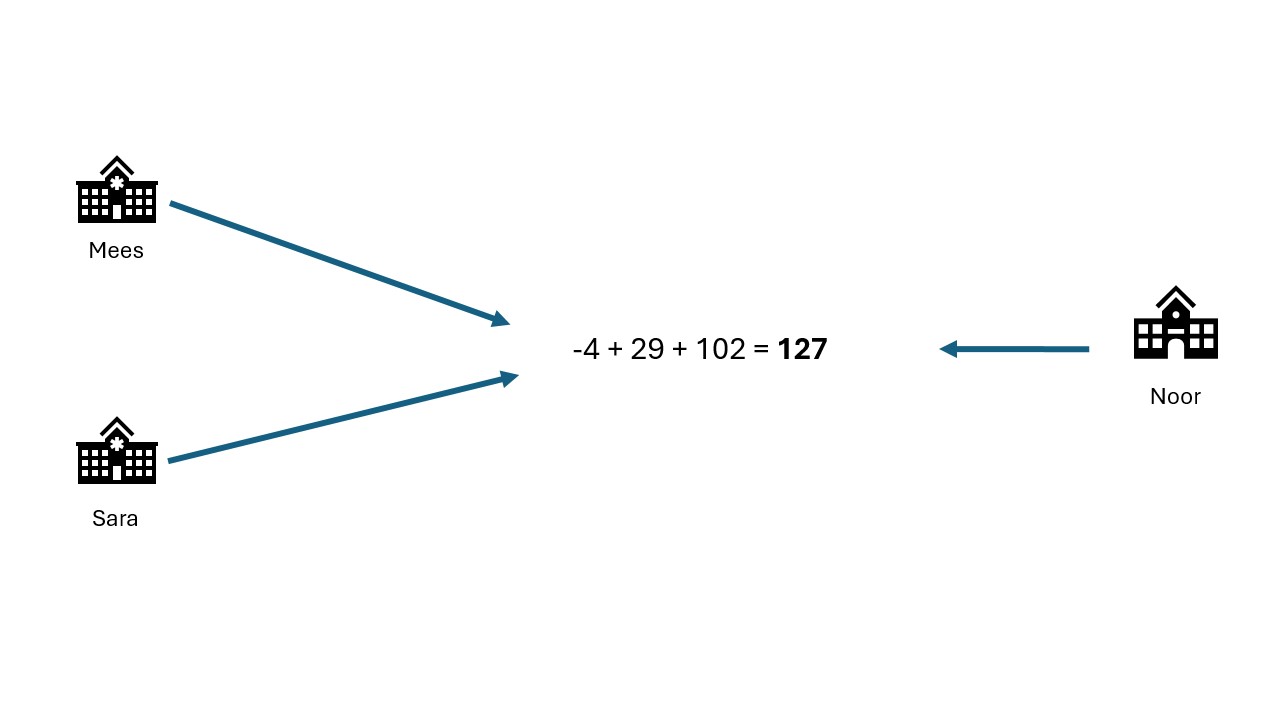
Mees, Sara and Noor add their shares together
for the final result
Figure 10
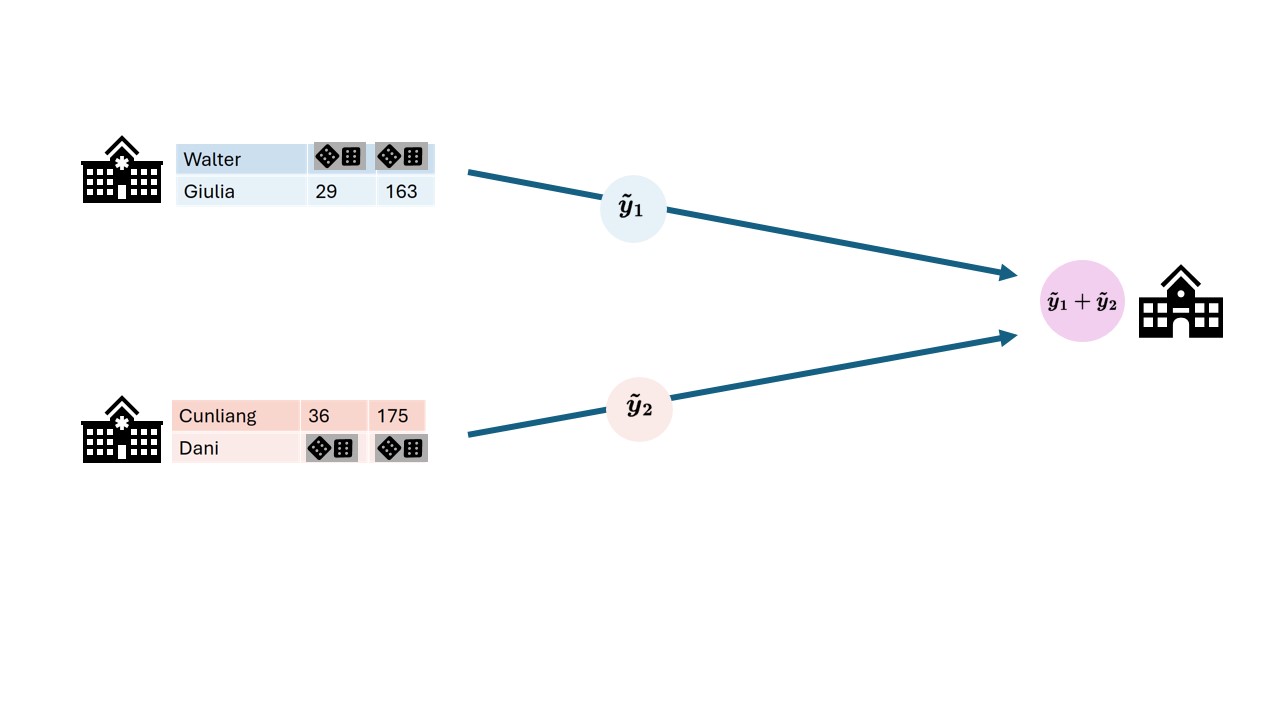
Differential privacy sometimes replaces a subset
of the data with random values
Figure 11
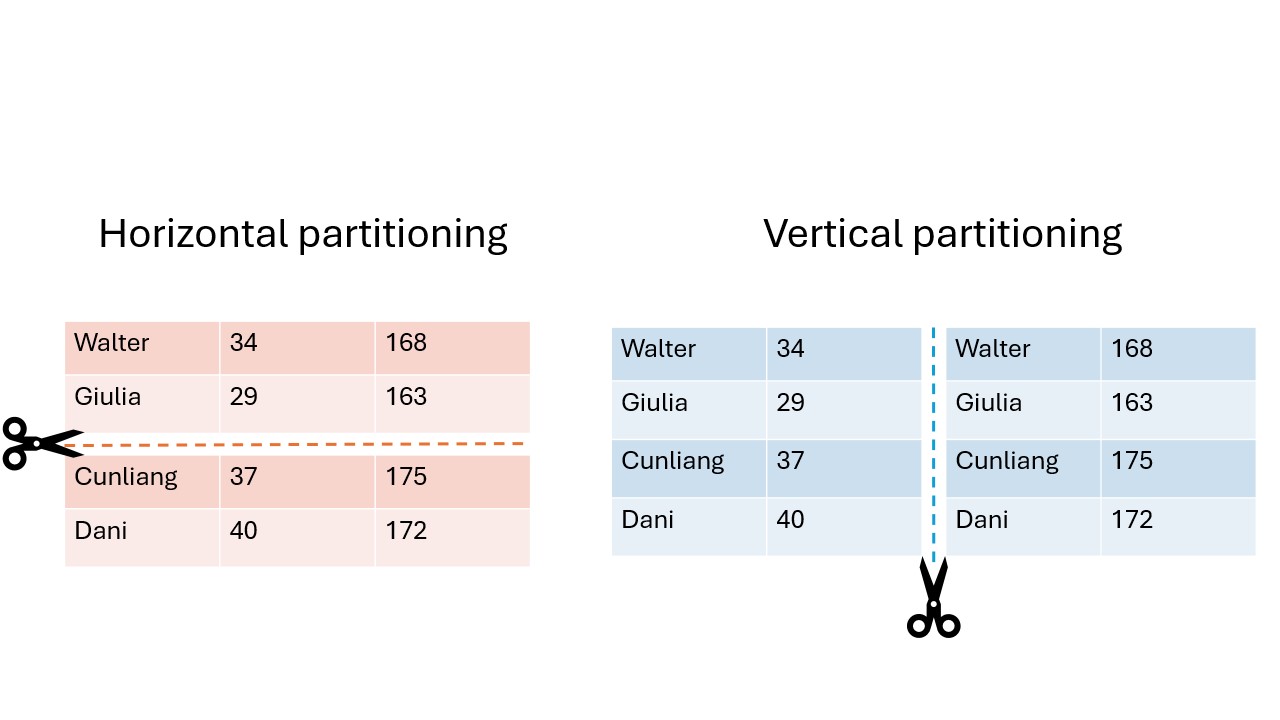
Horizontal and vertical partitioning refers to
how data is separated
vantage6 basics
Figure 1
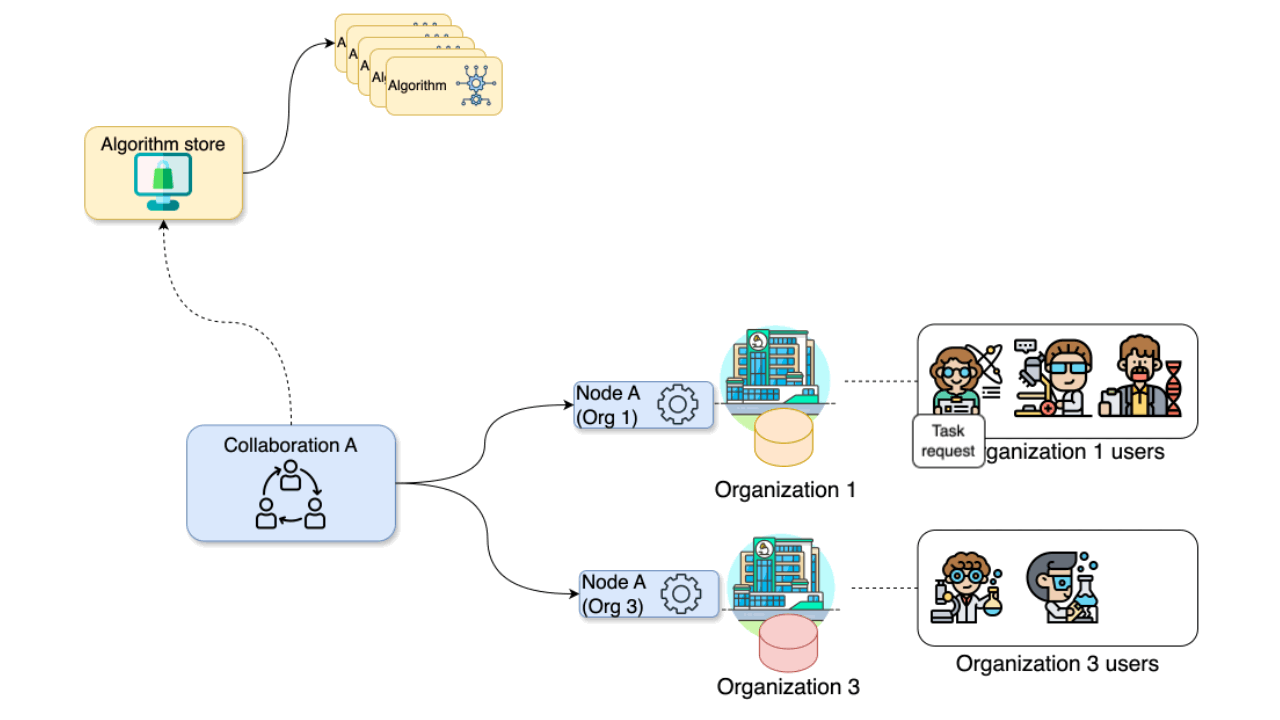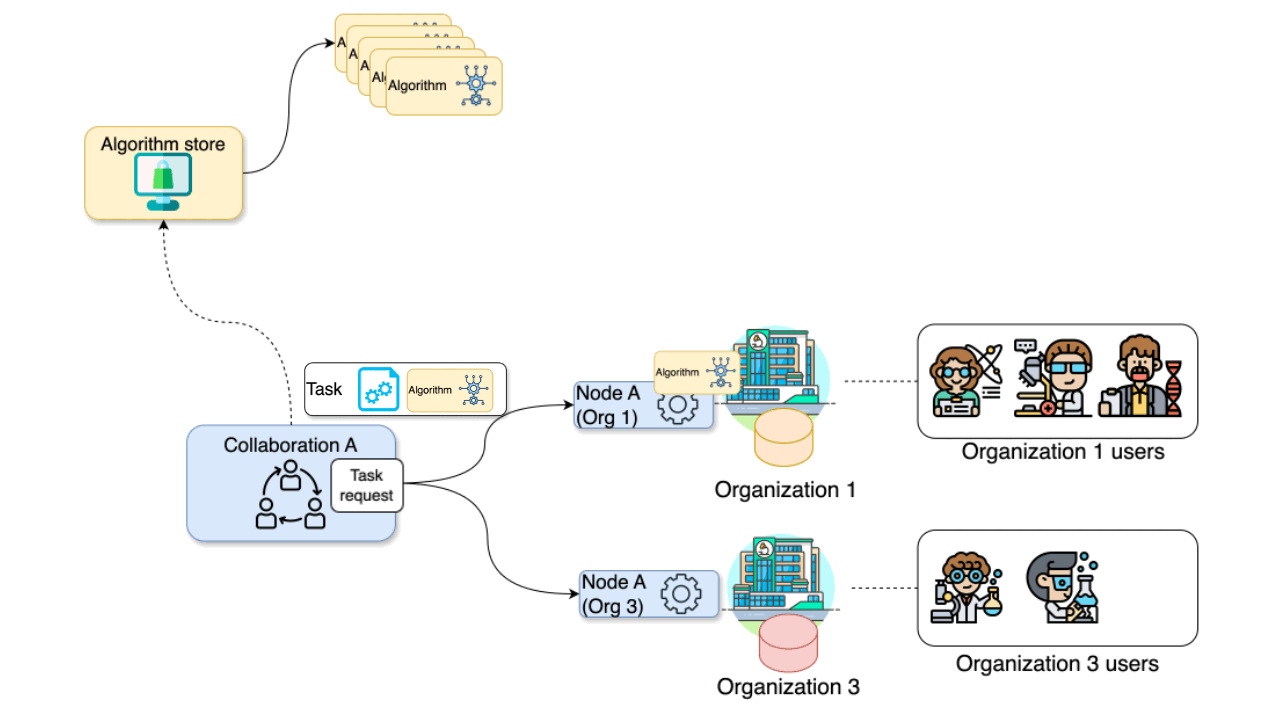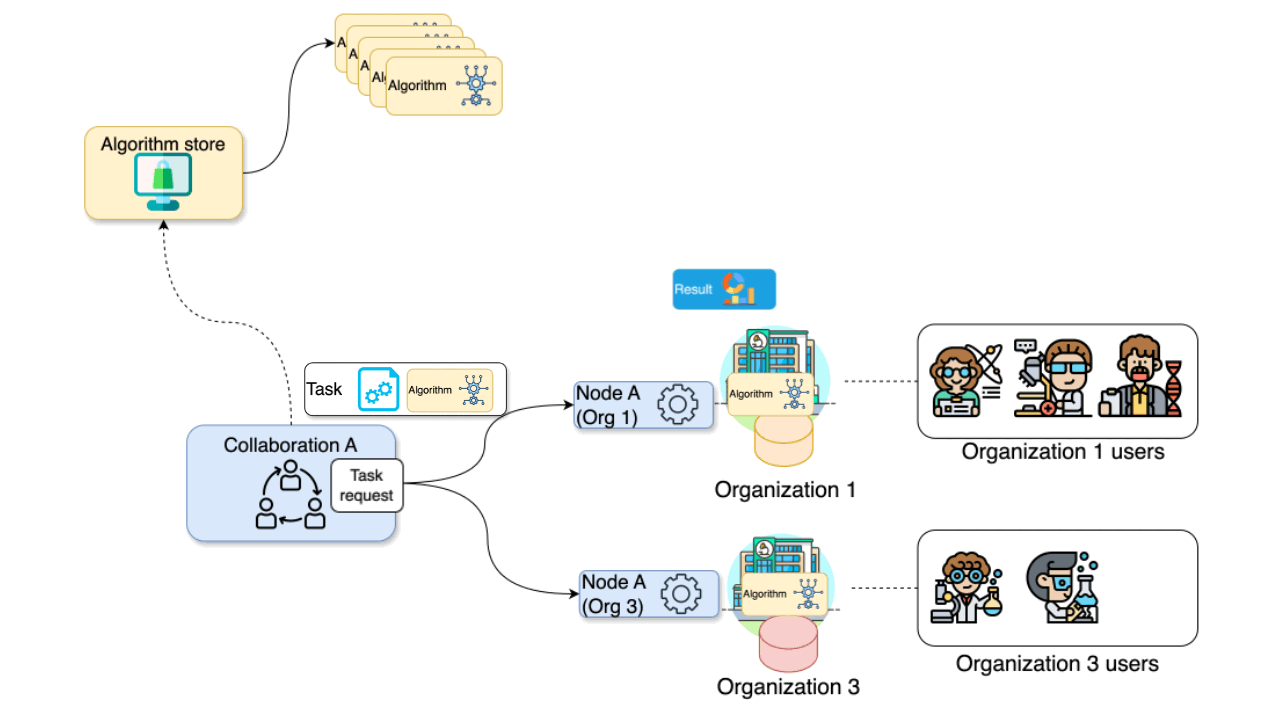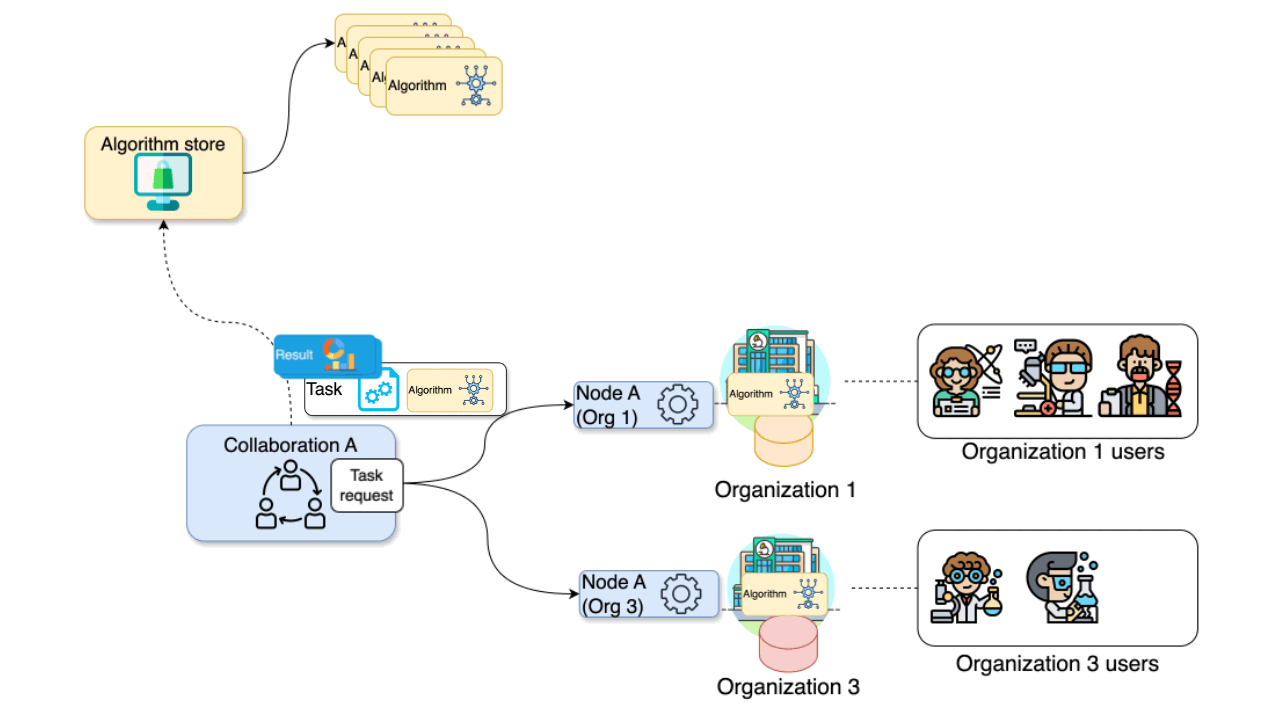
Figure 2
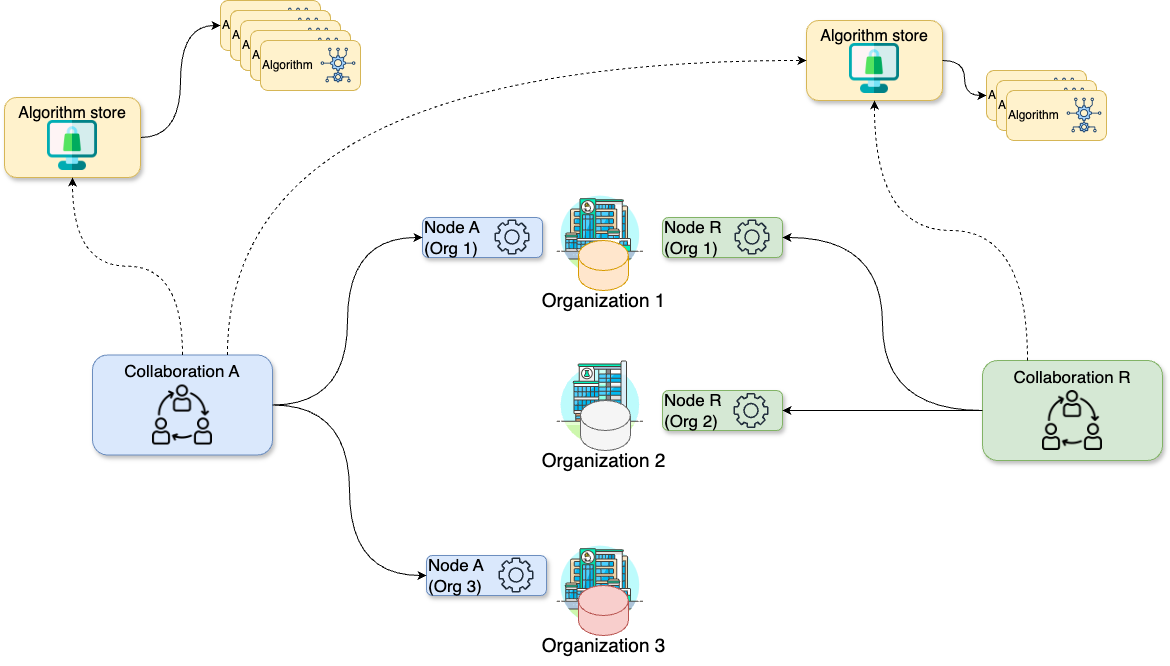
Figure 3
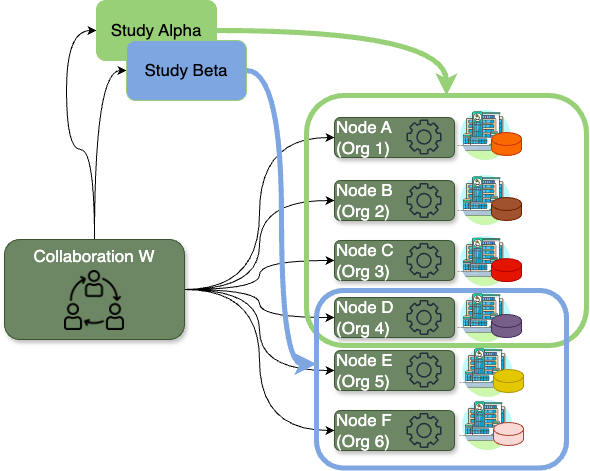
Figure 4
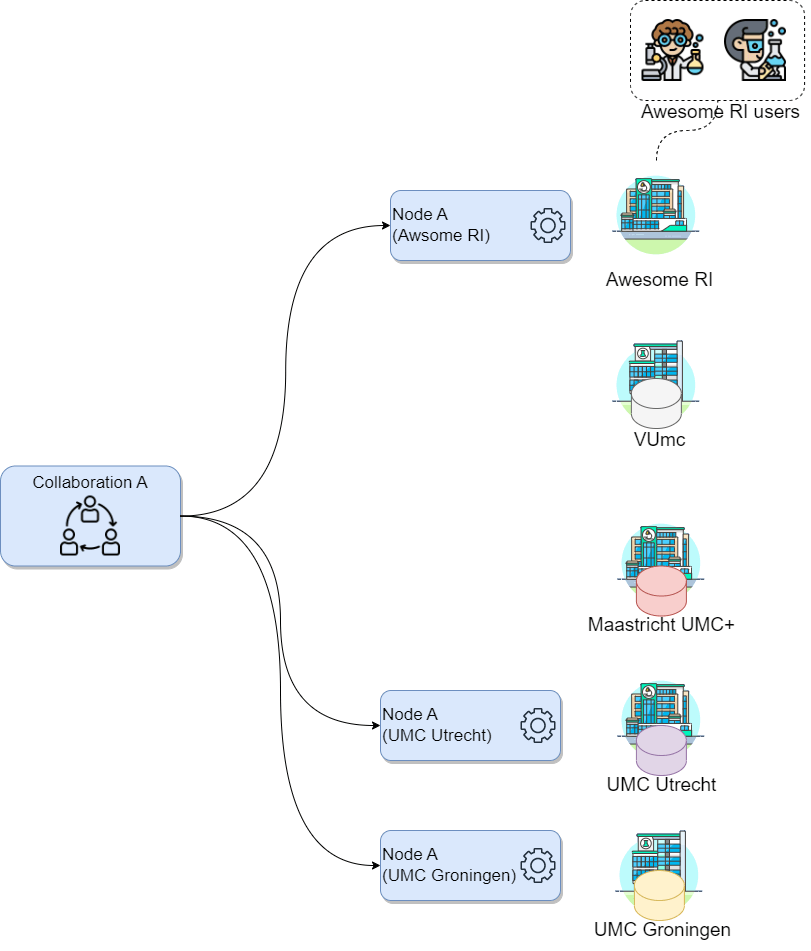
Figure 5
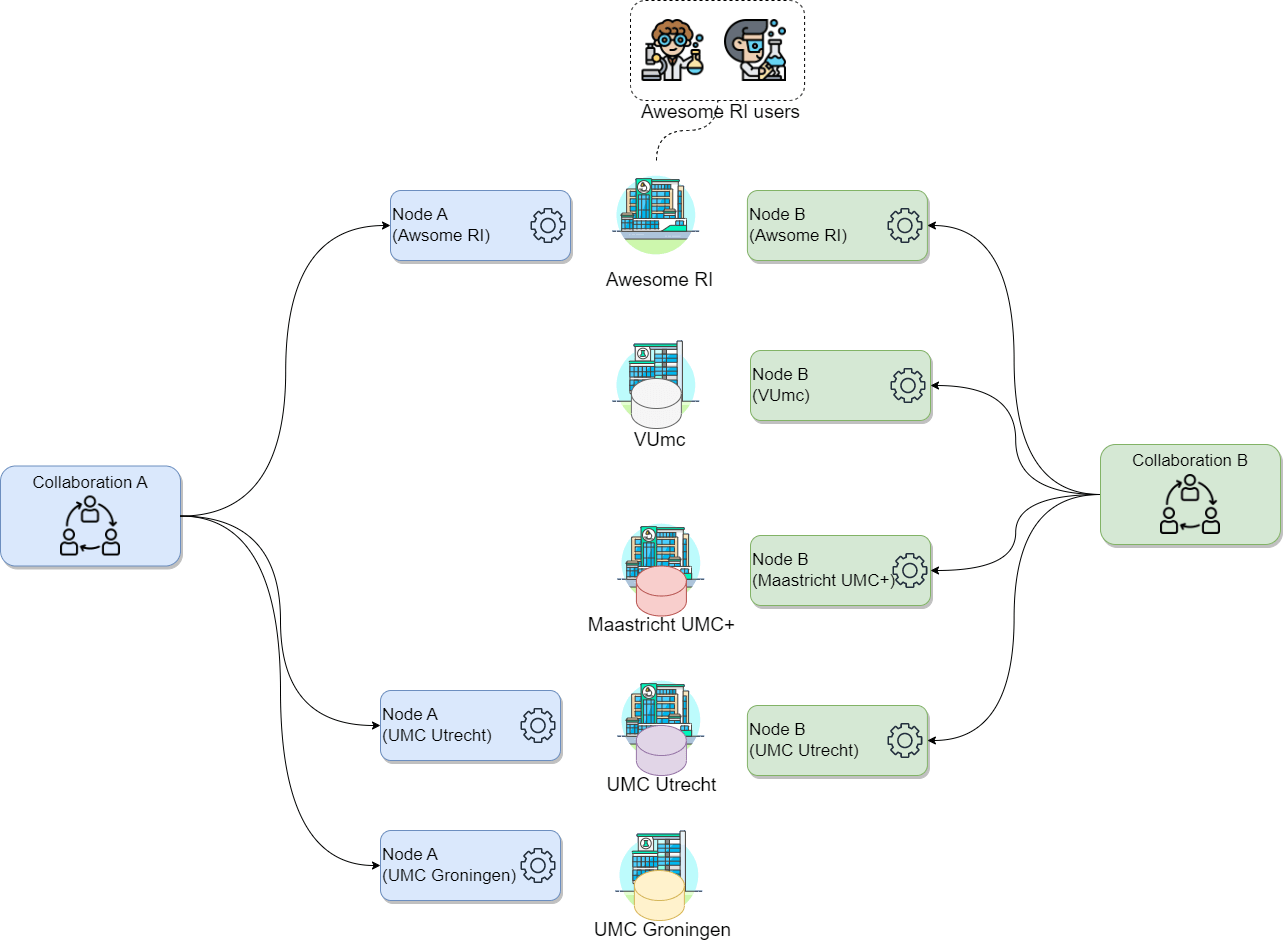
Figure 6
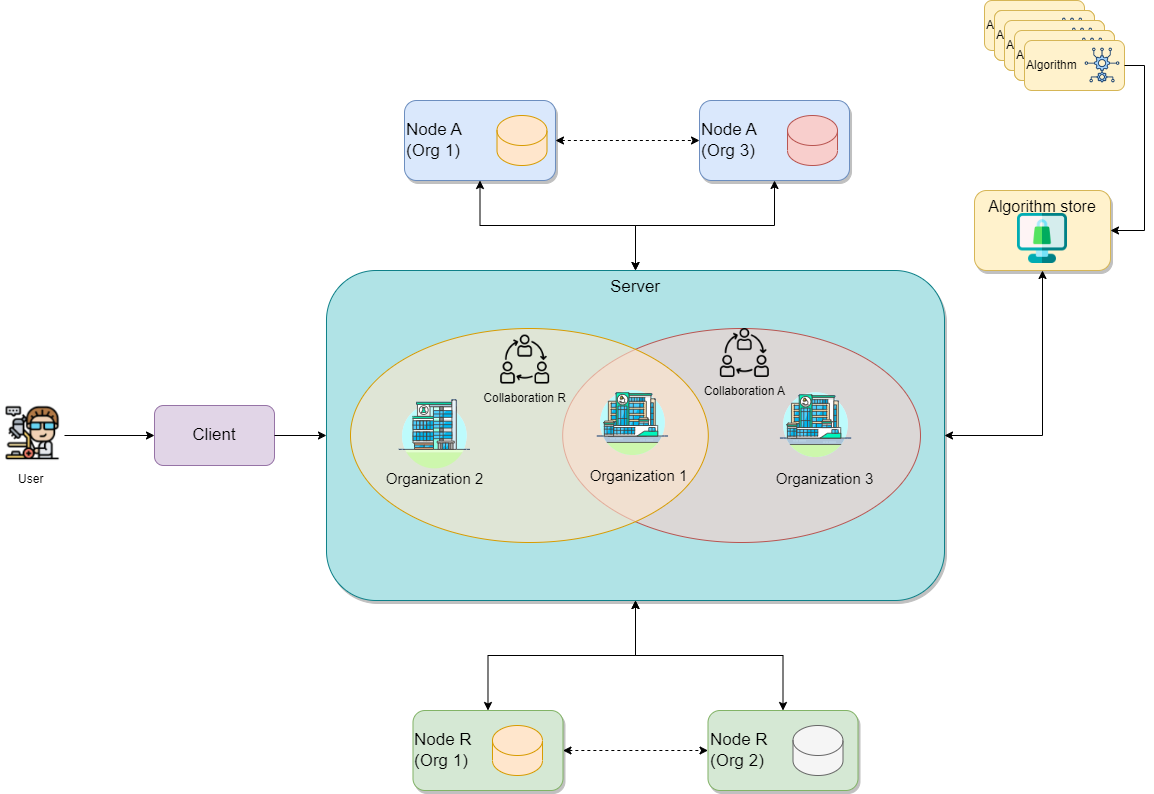
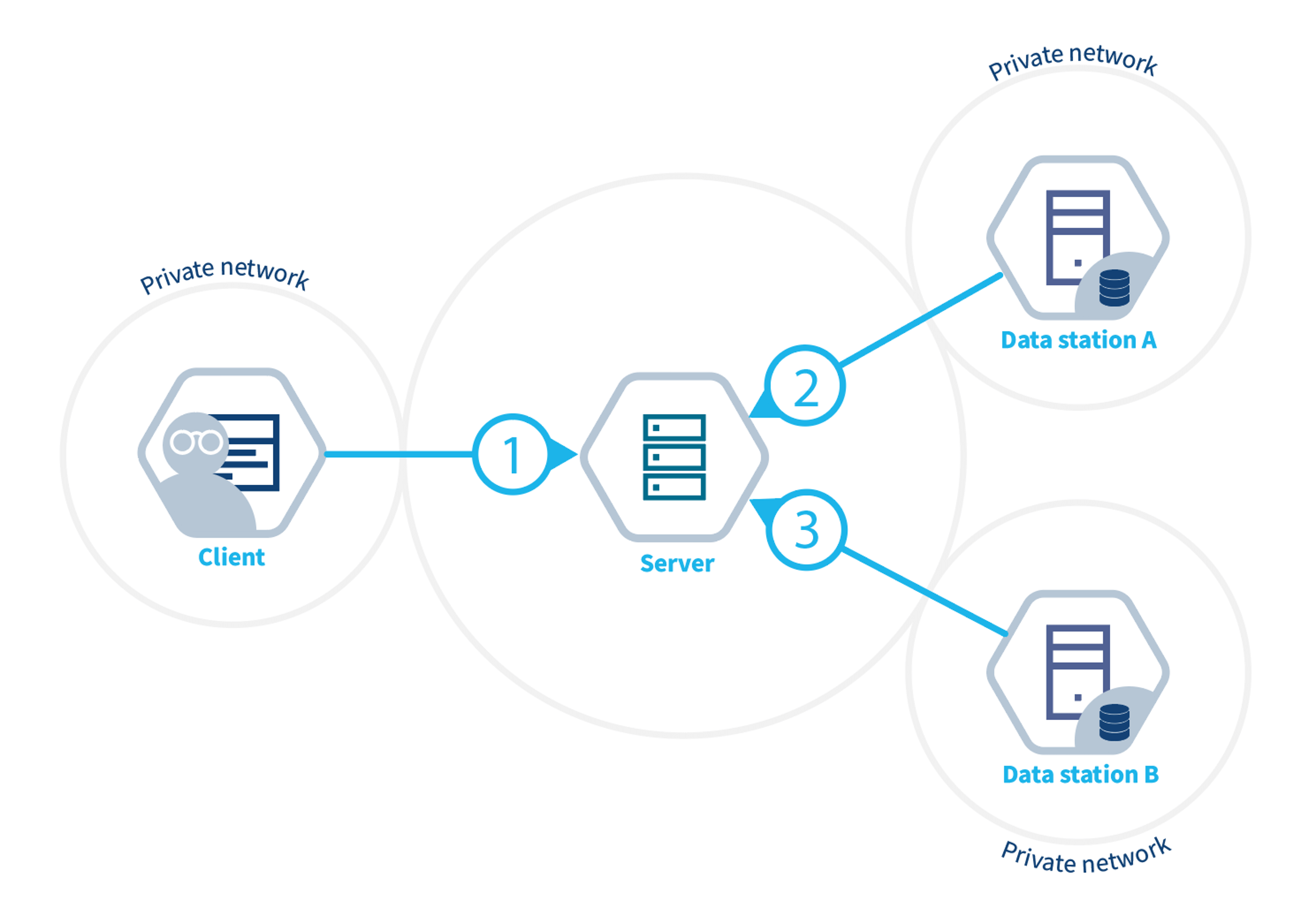
High level overview of the vantage6
infrastructure. Client(s) and node(s) communicate through the Server.
Nodes are able to communicate directly with each other when the optional
VPN feature is enabled.
Figure 7
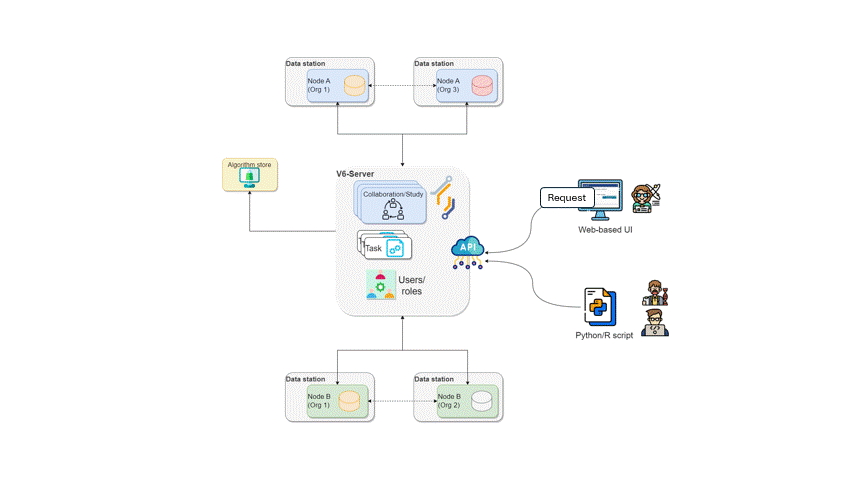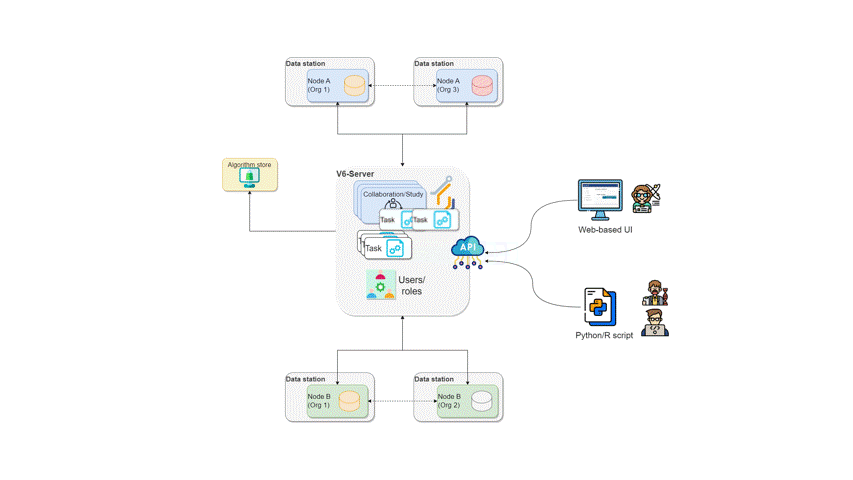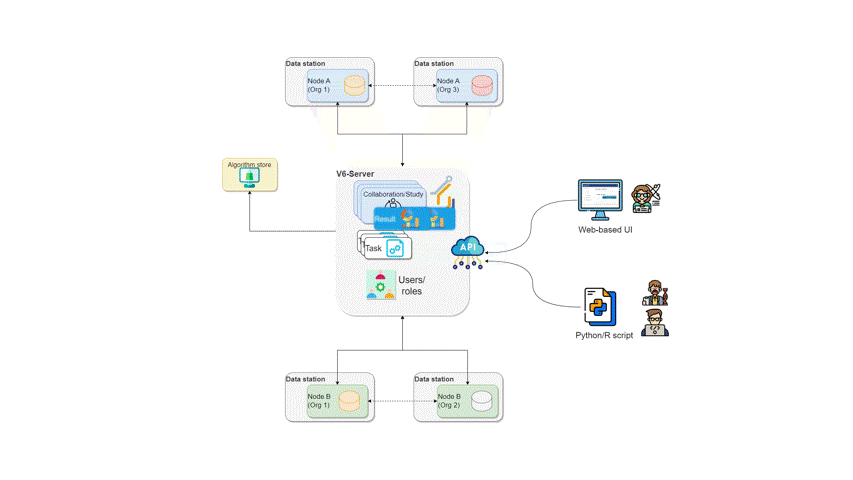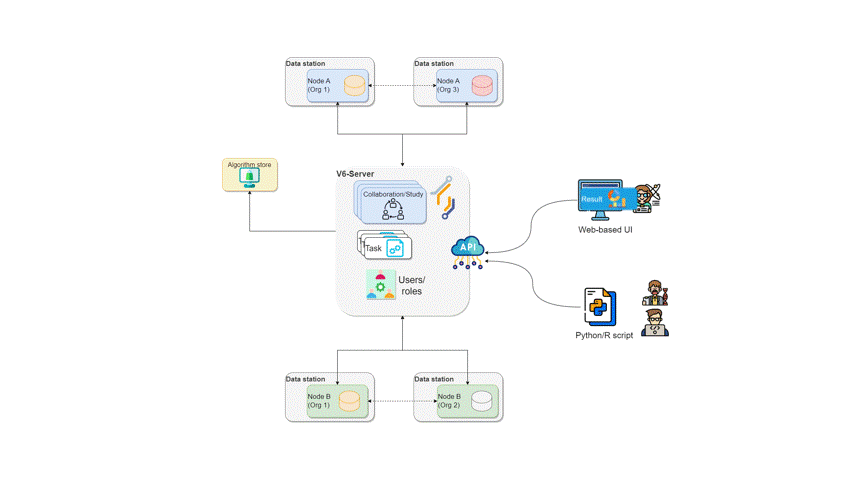
Figure 8
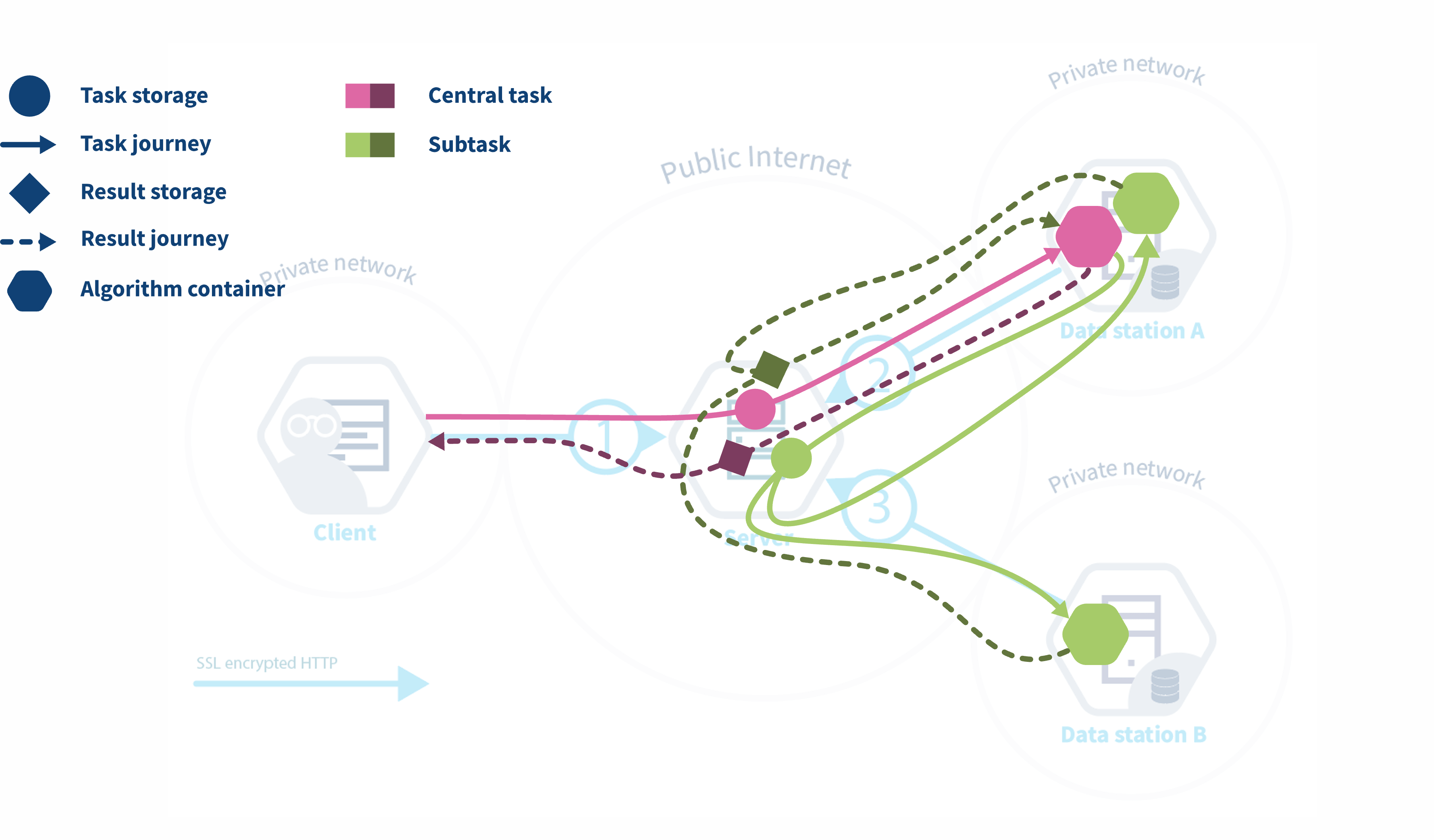
Federated analysis orchestrated by
vantage6
Figure 9
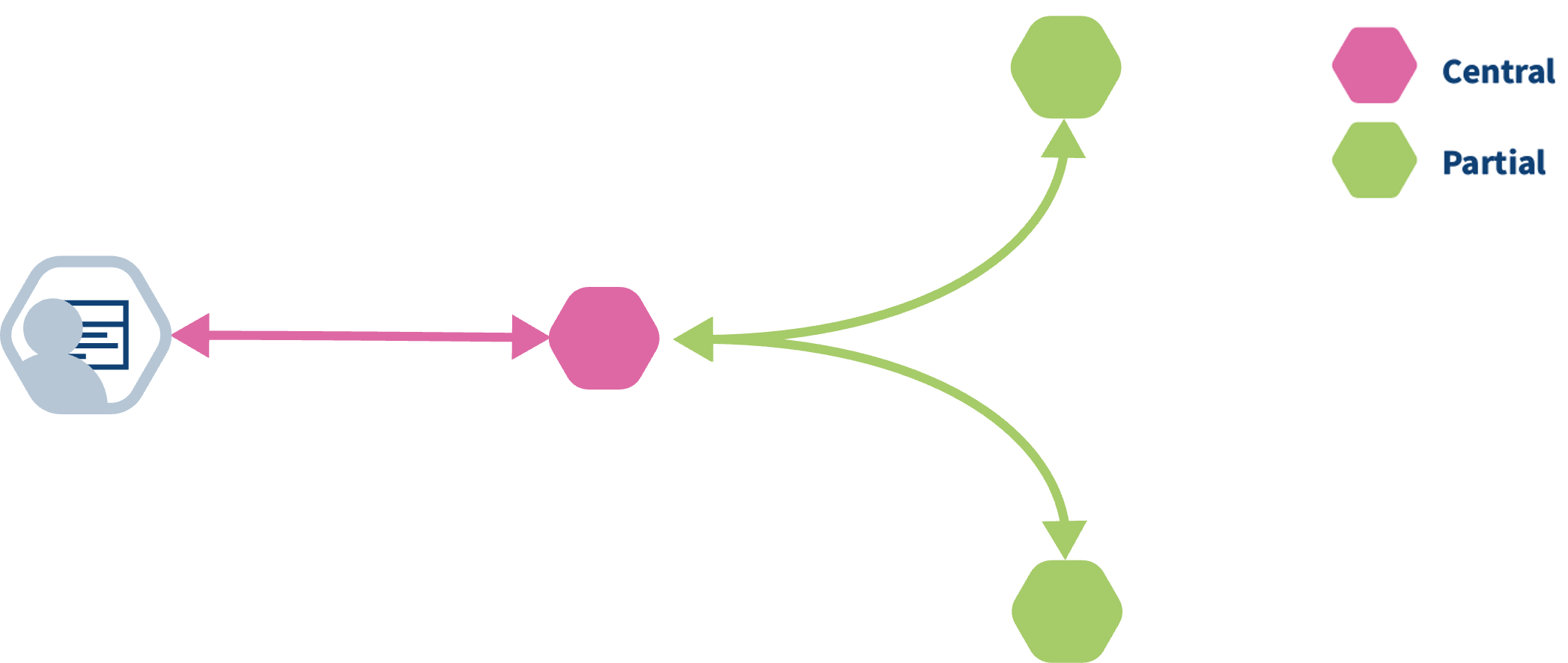
vantage6 central and federated tasks.
Figure 10
Architecture.
Figure 11
vantage6 algorithm workflow.
Running a PET analysis without programming on vantage6
Figure 1
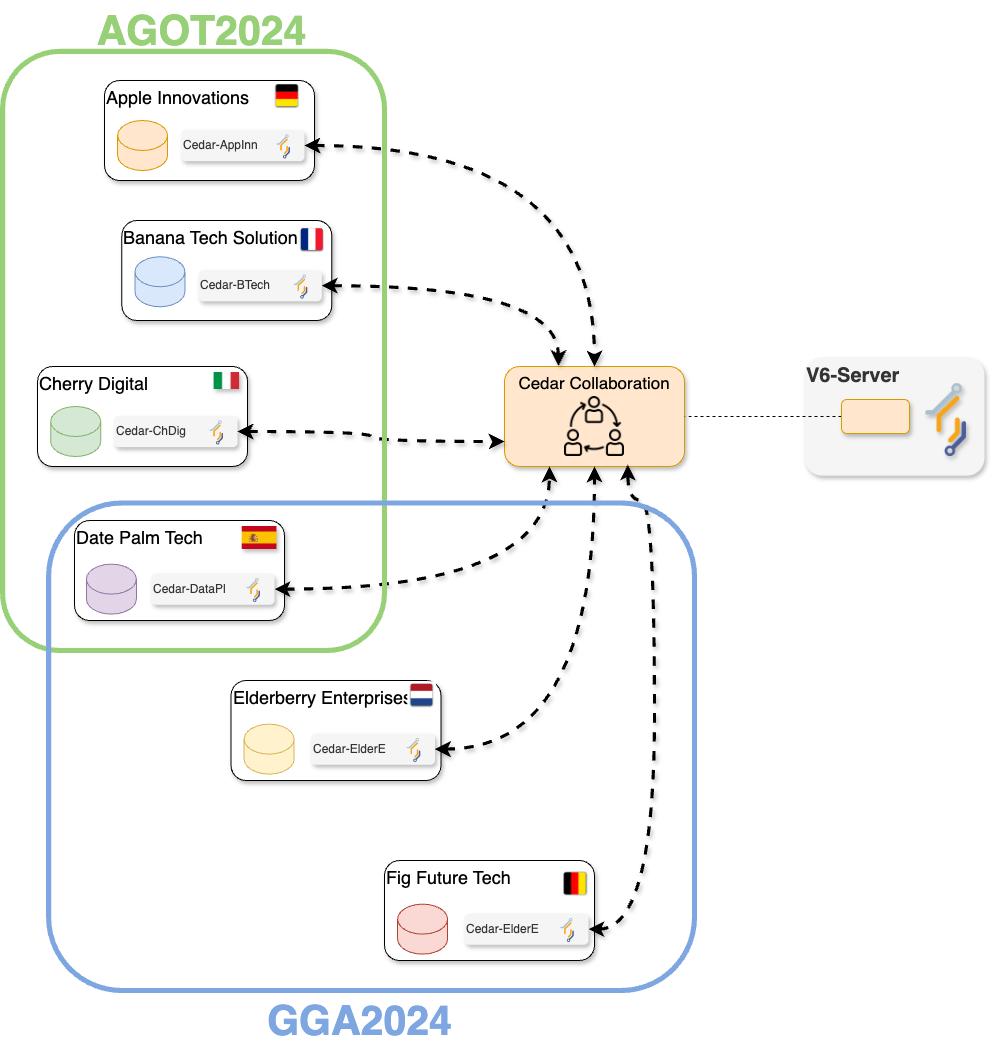
Hypothetical collaborations scenario
Figure 2
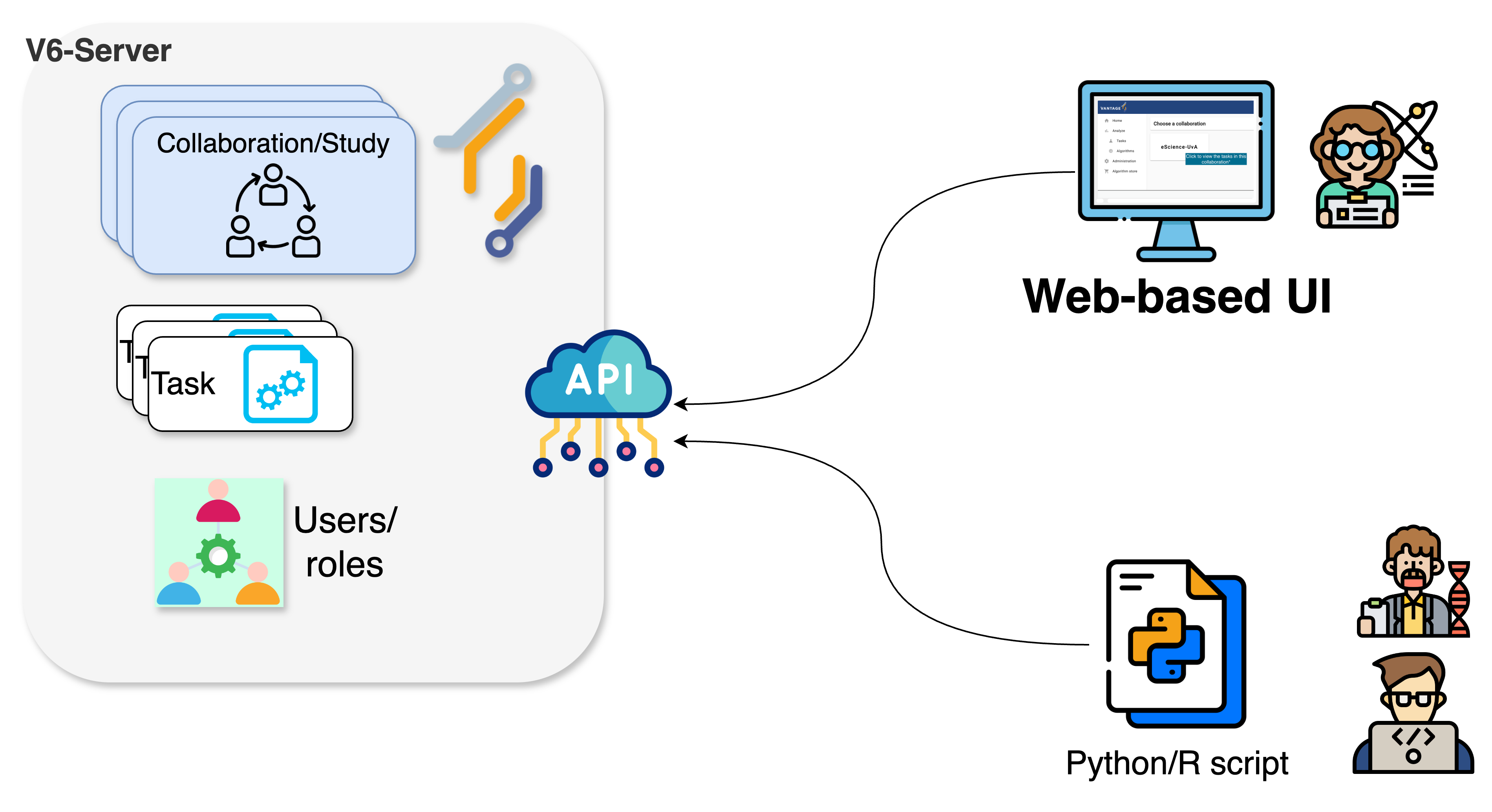
Vantage6 API clients
Figure 3
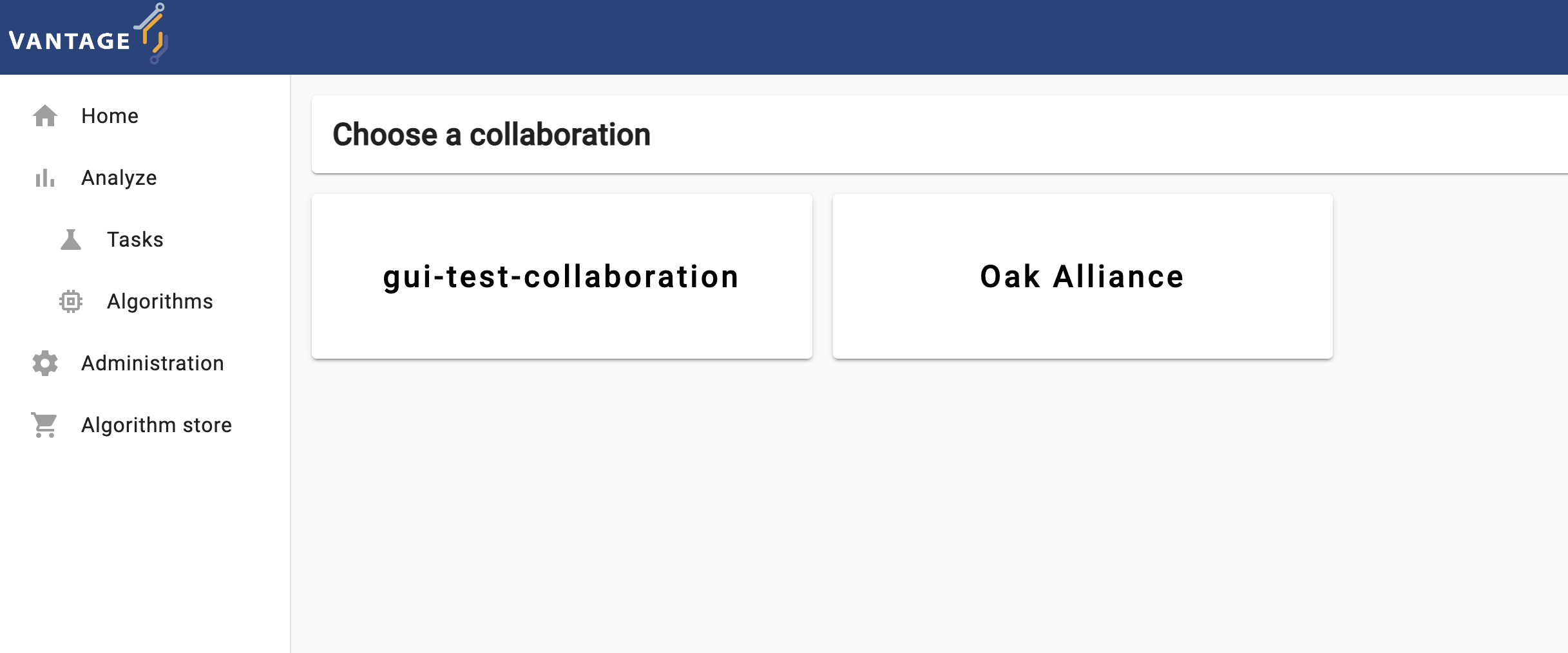
vantage6 UI start page
Figure 4
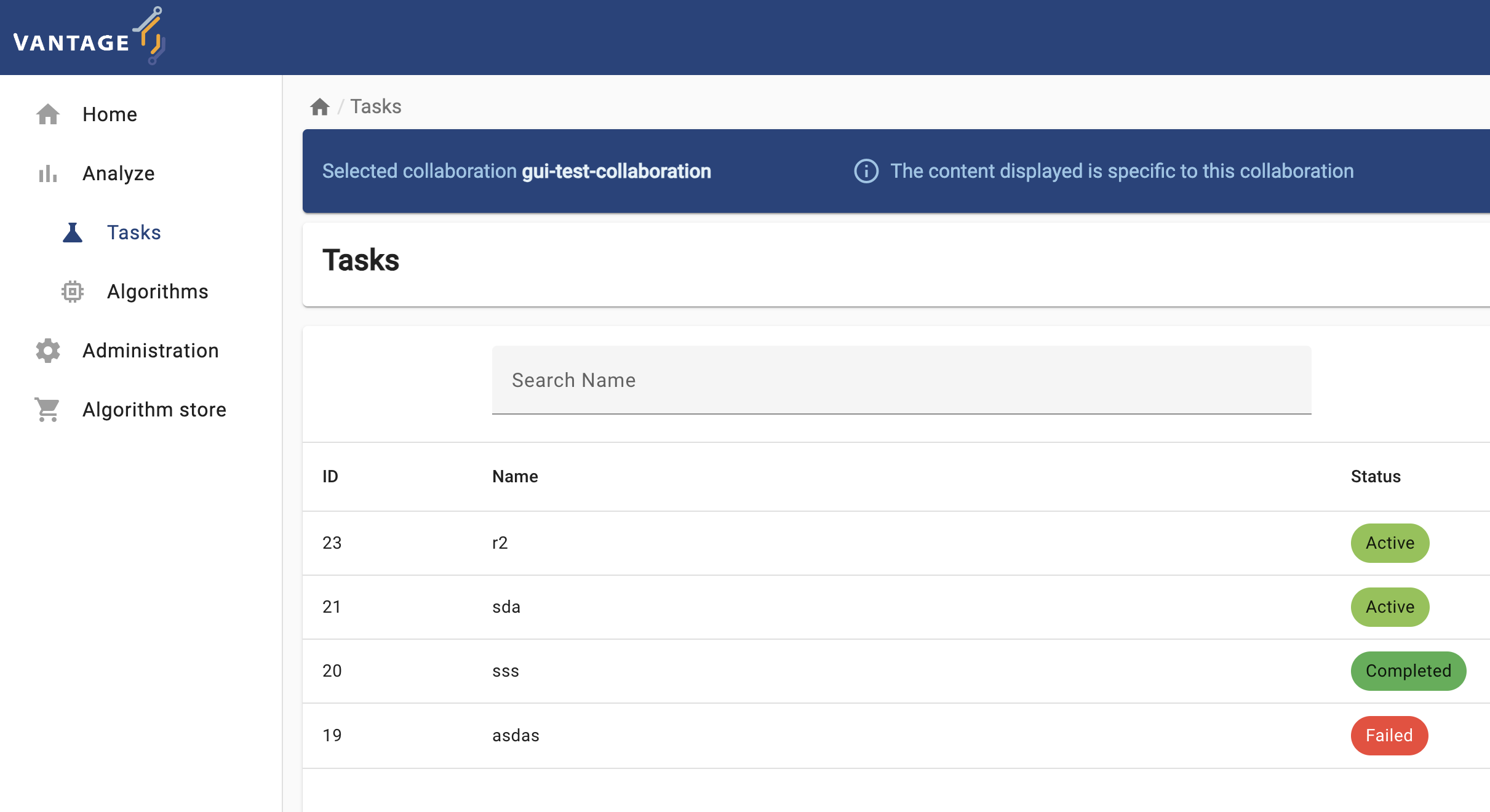
vantage6 UI tasks page
Figure 5
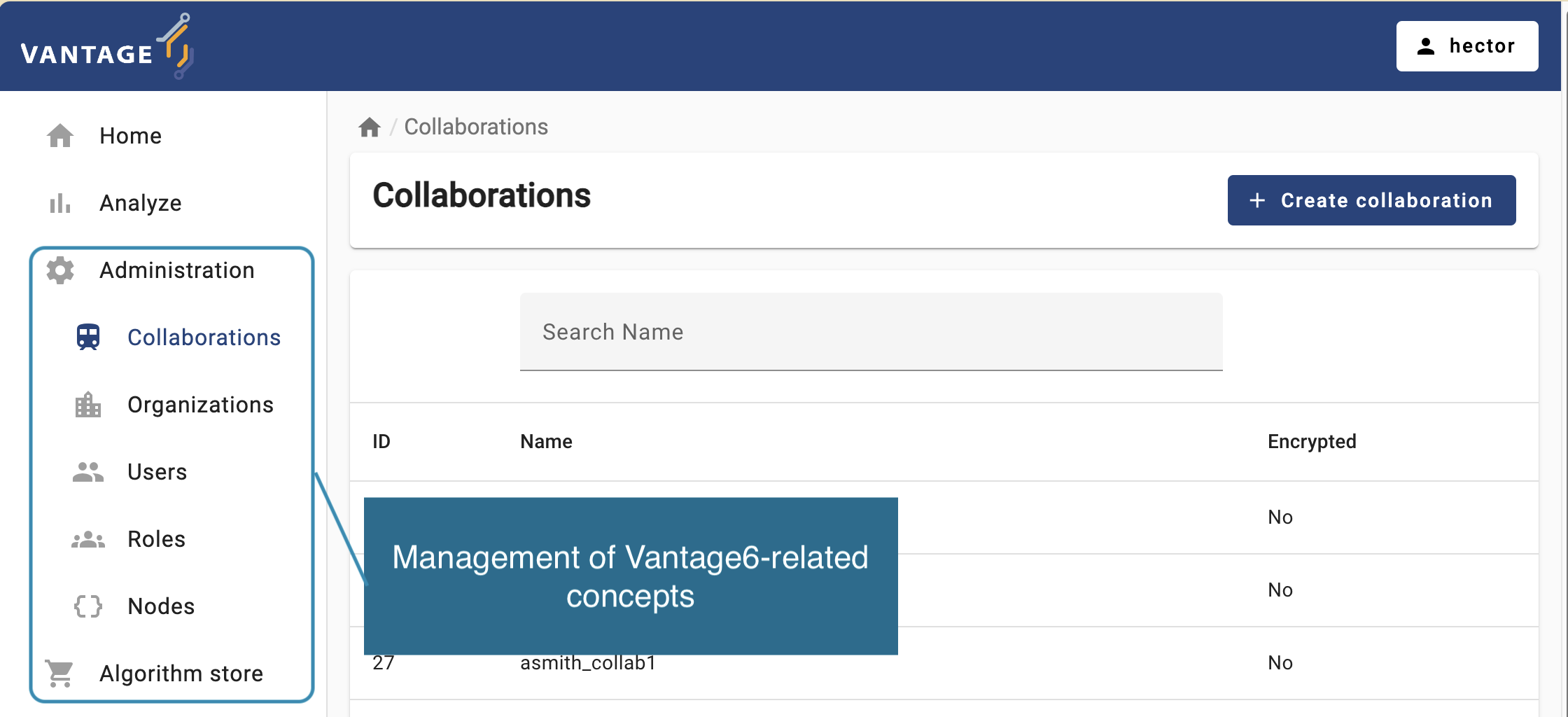
vantage6 UI administration page
Figure 6
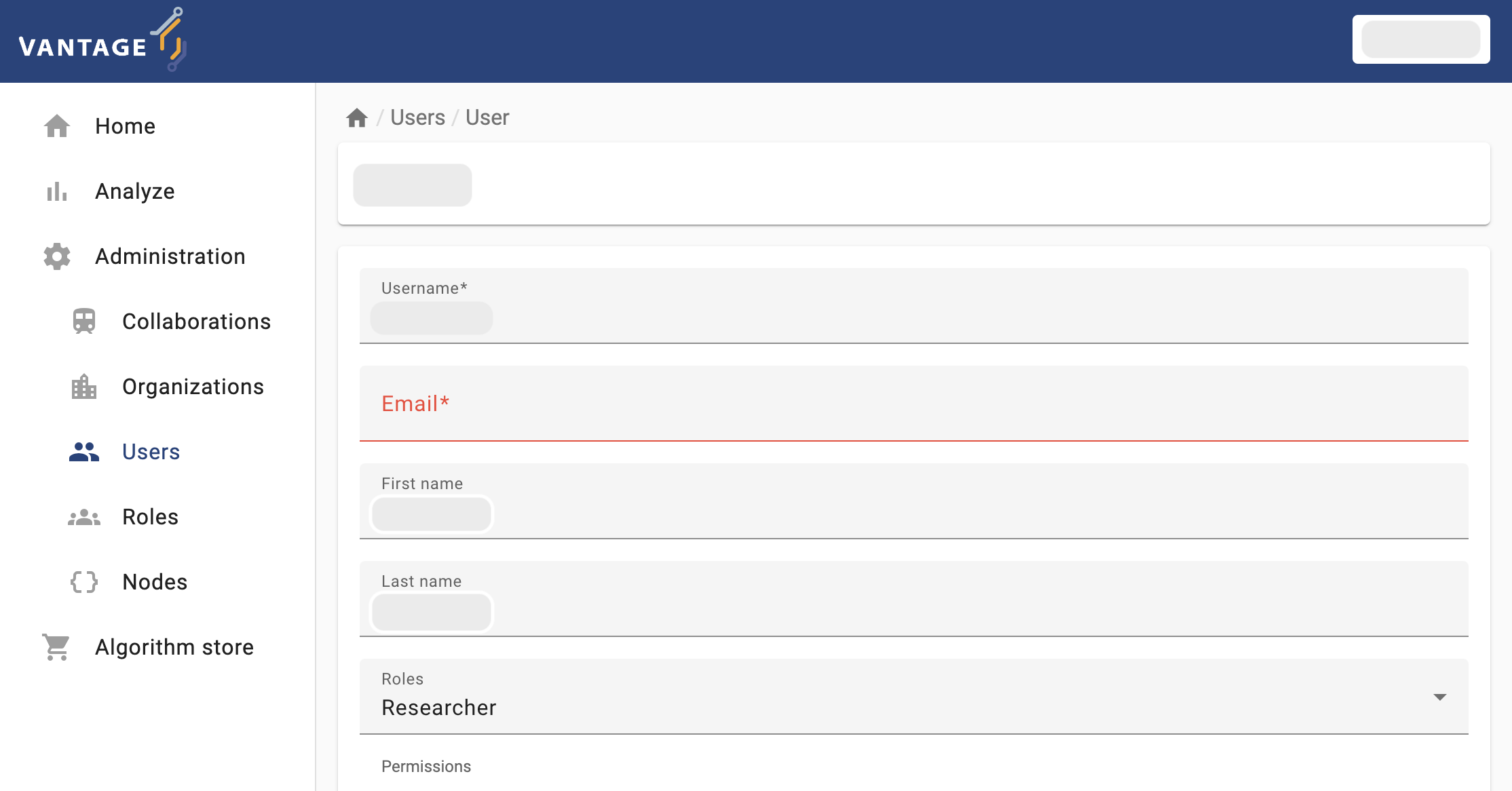
User-entity - edit option
Figure 7
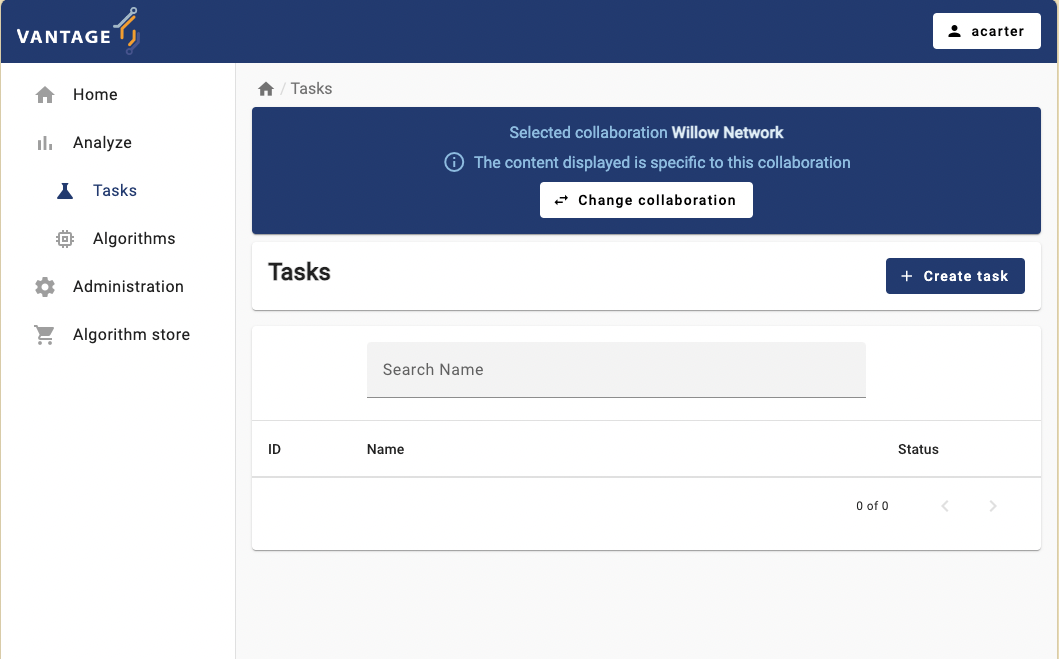
Figure 8
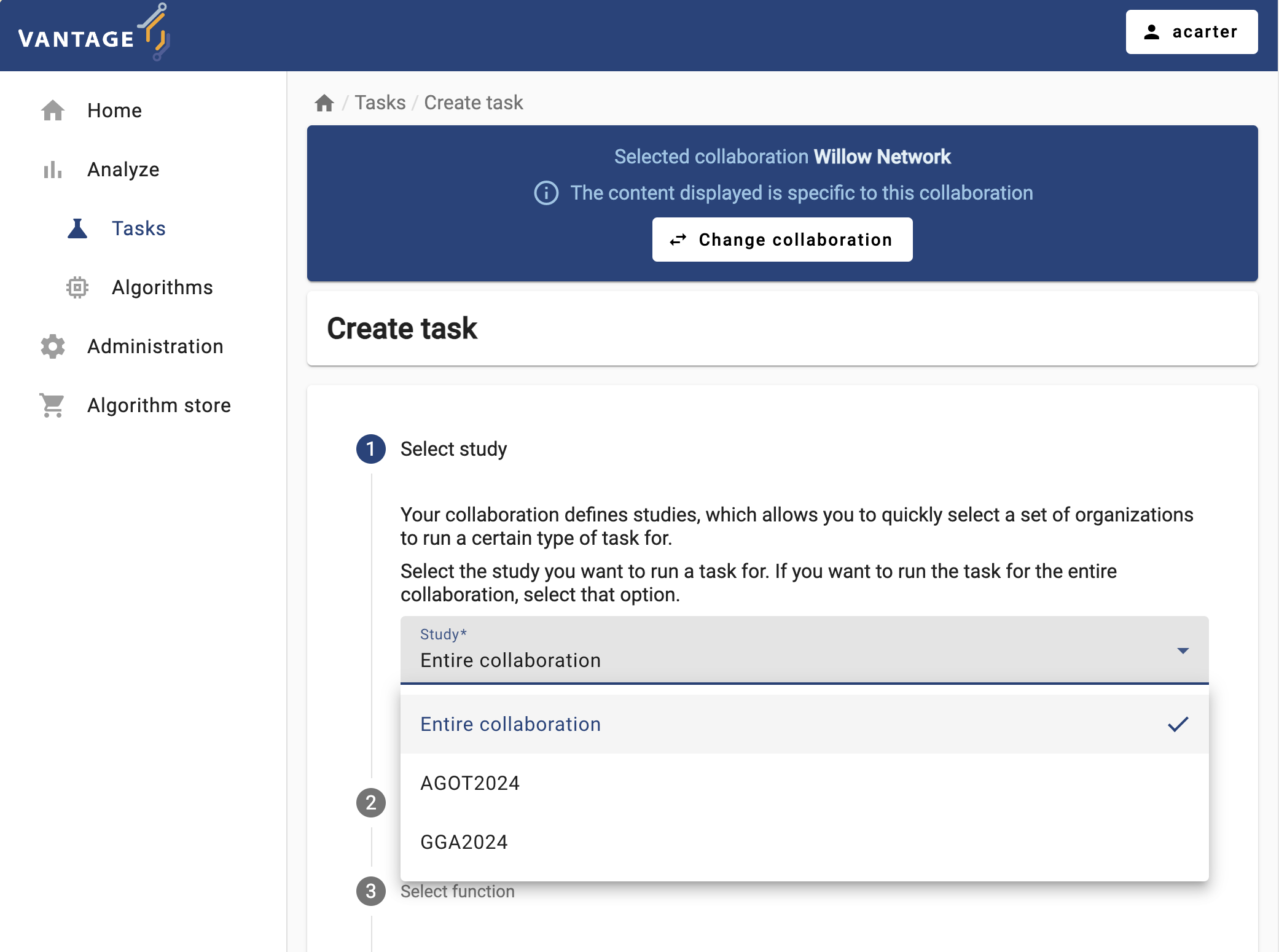
Figure 9
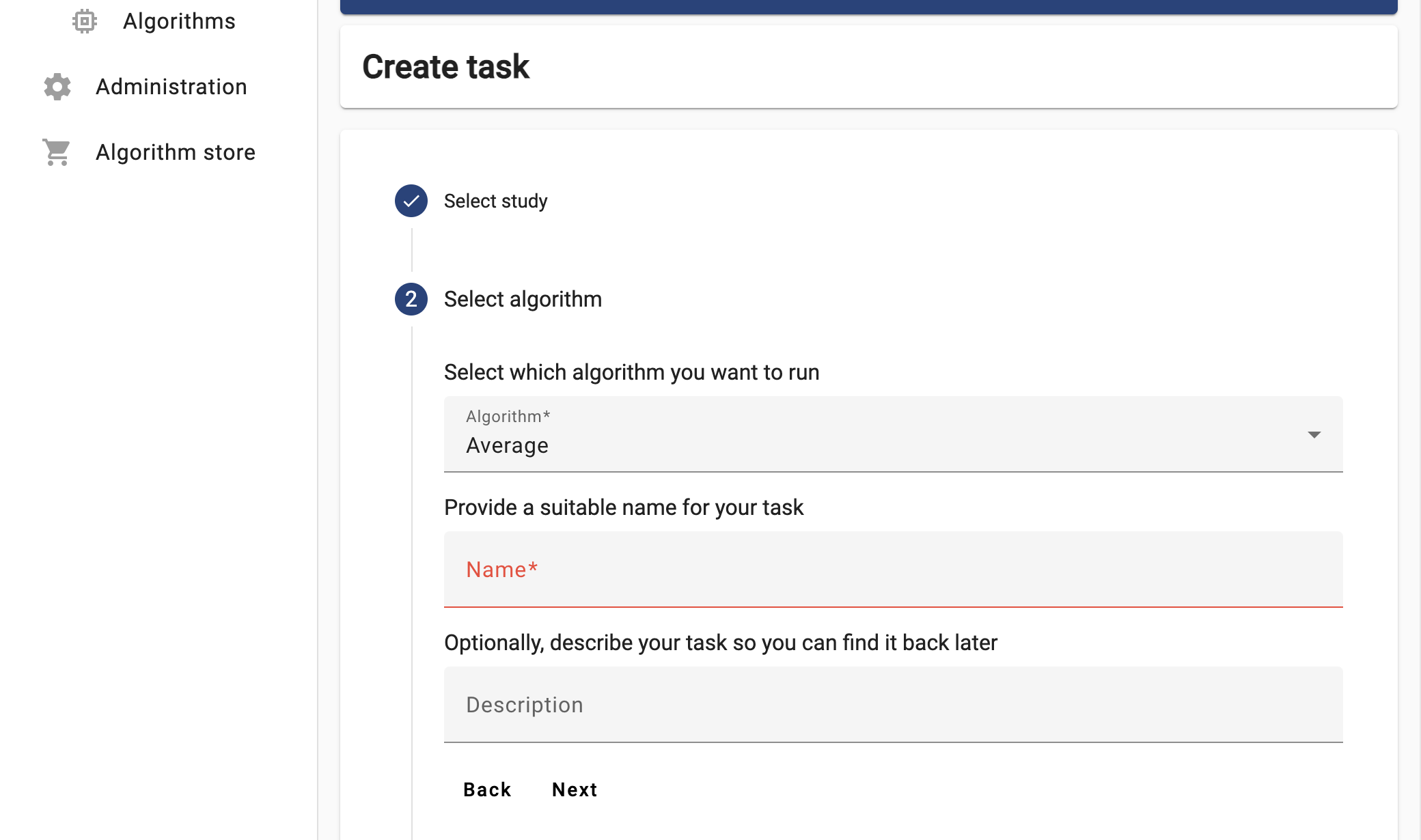
Figure 10
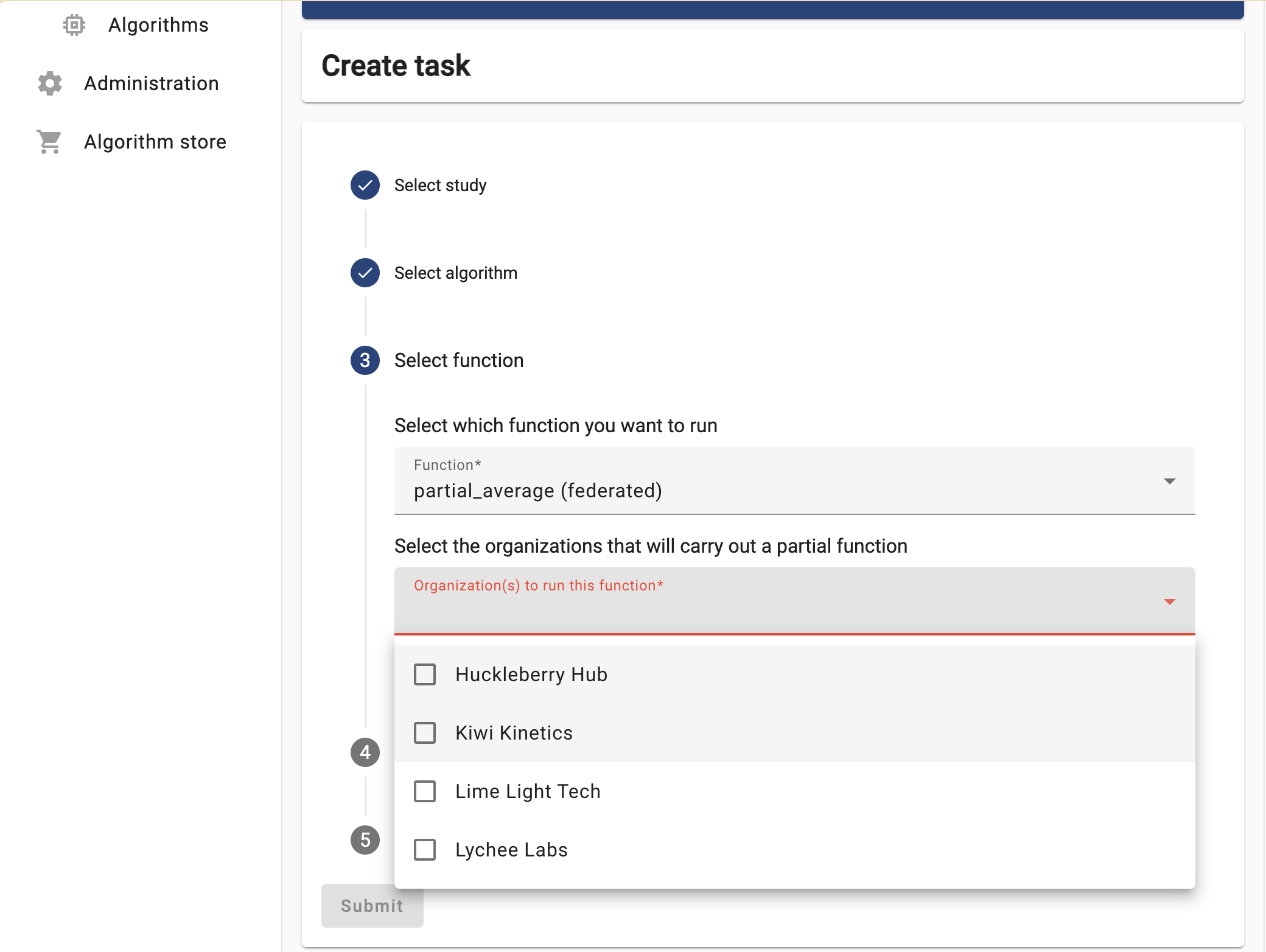
Figure 11
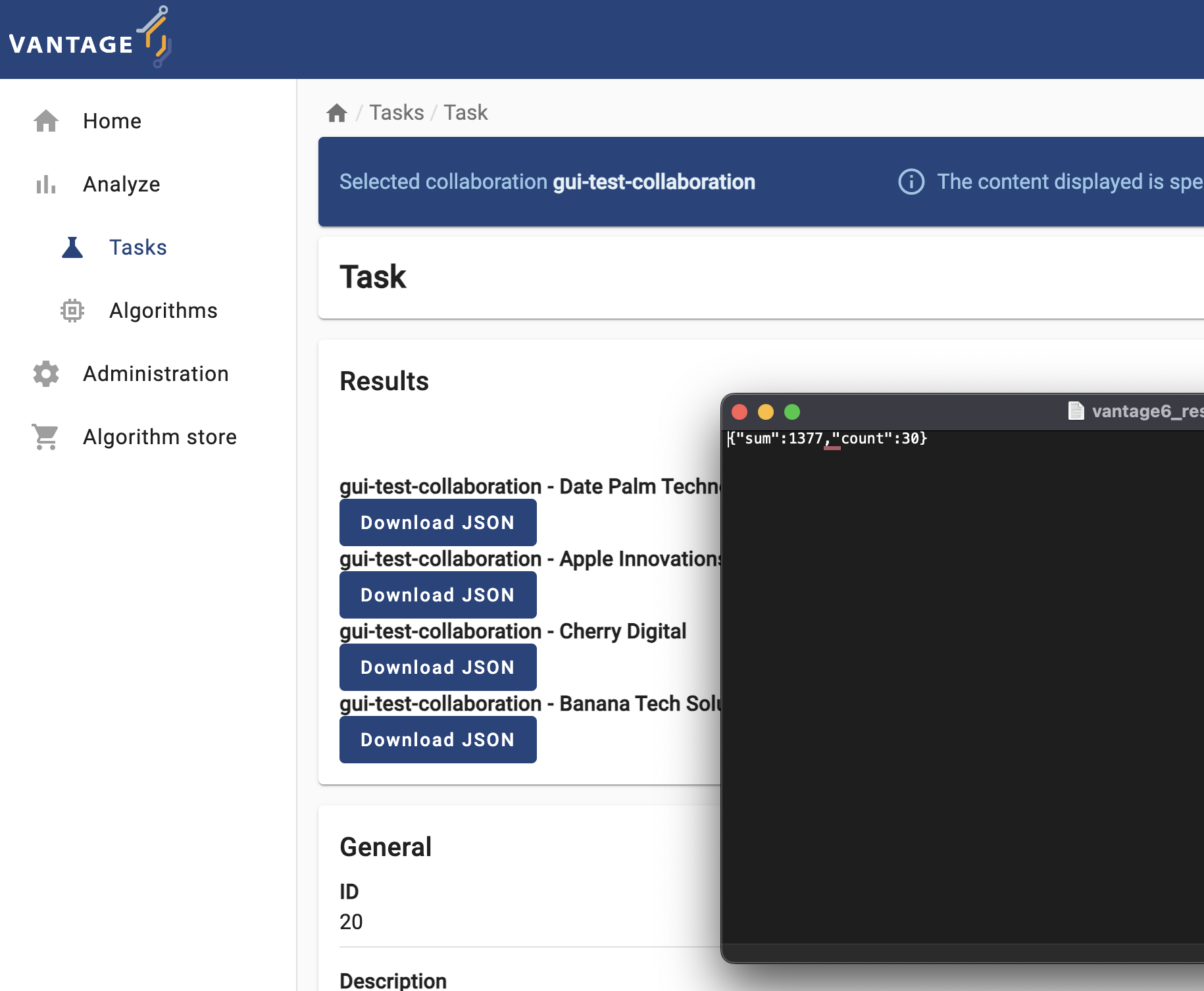
Results
Figure 12

Figure 13

Figure 14
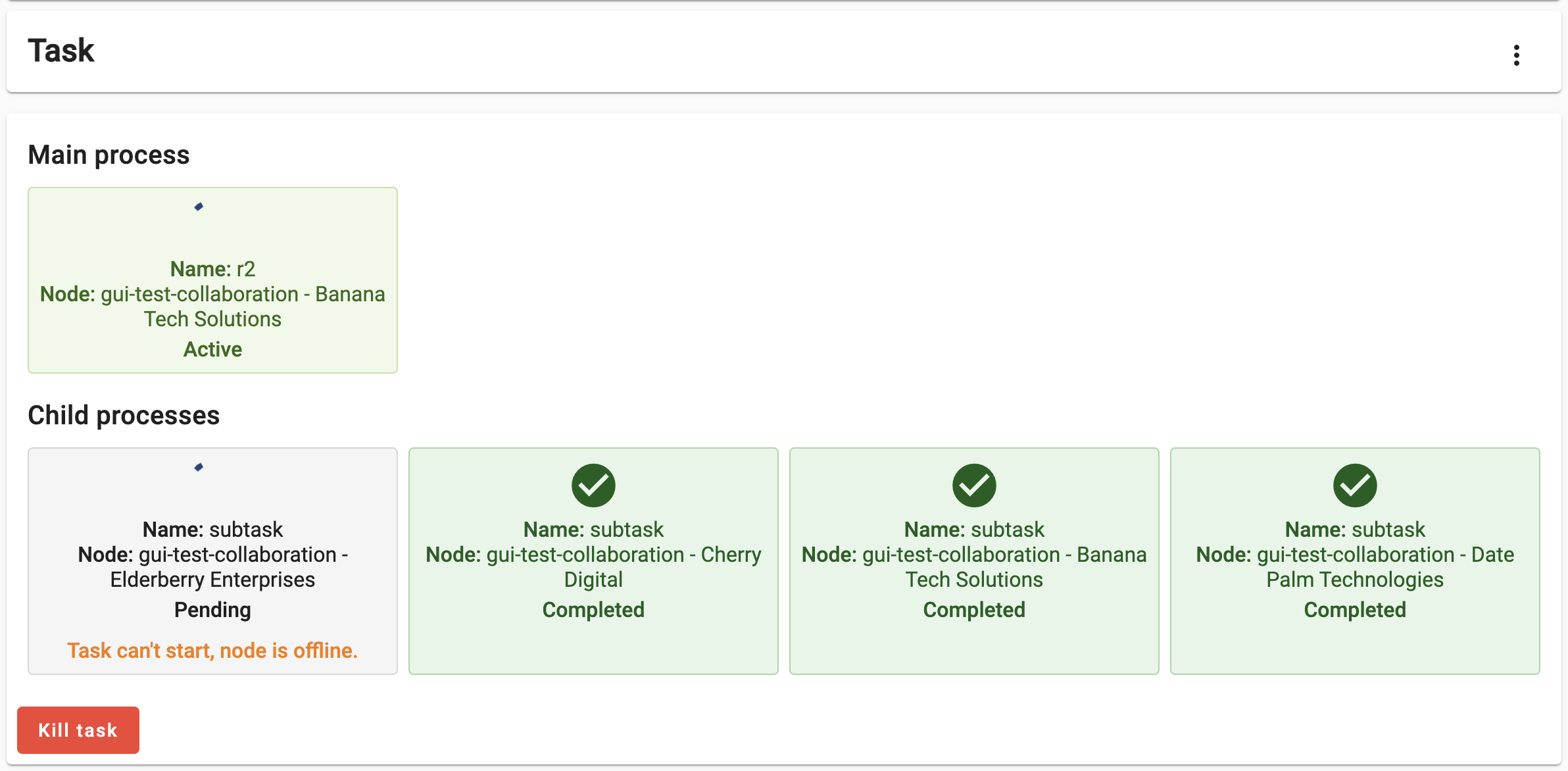
Figure 15
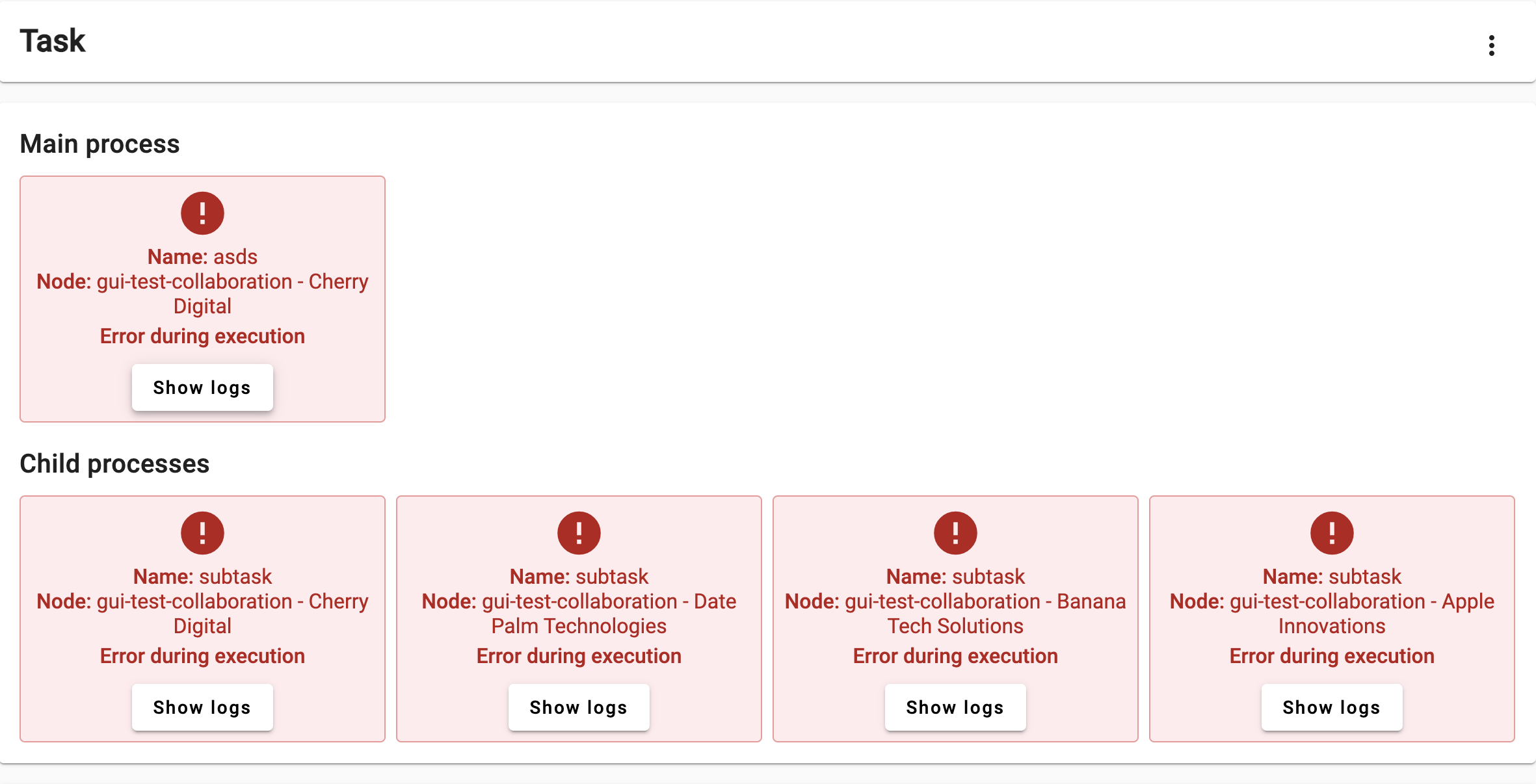
Figure 16
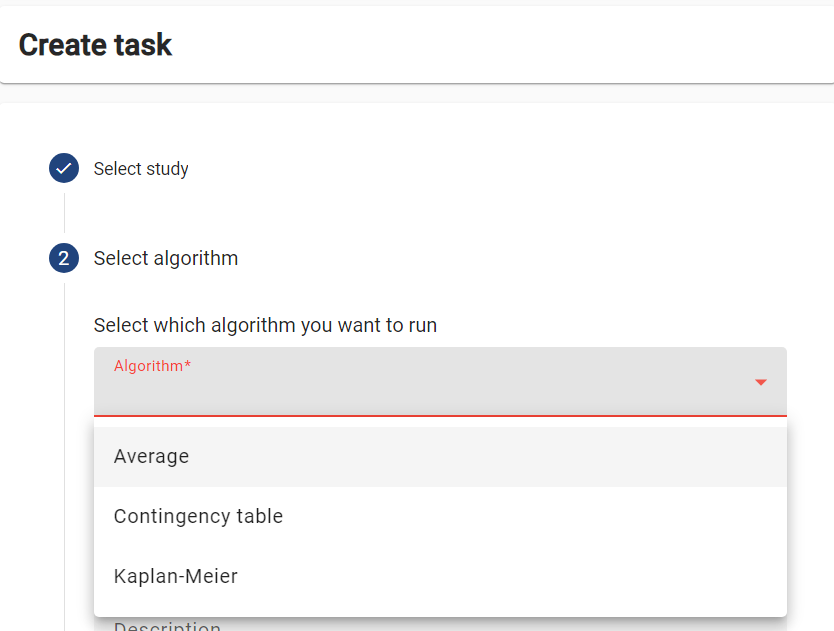
Managing vantage6 server via the user interface
Figure 1
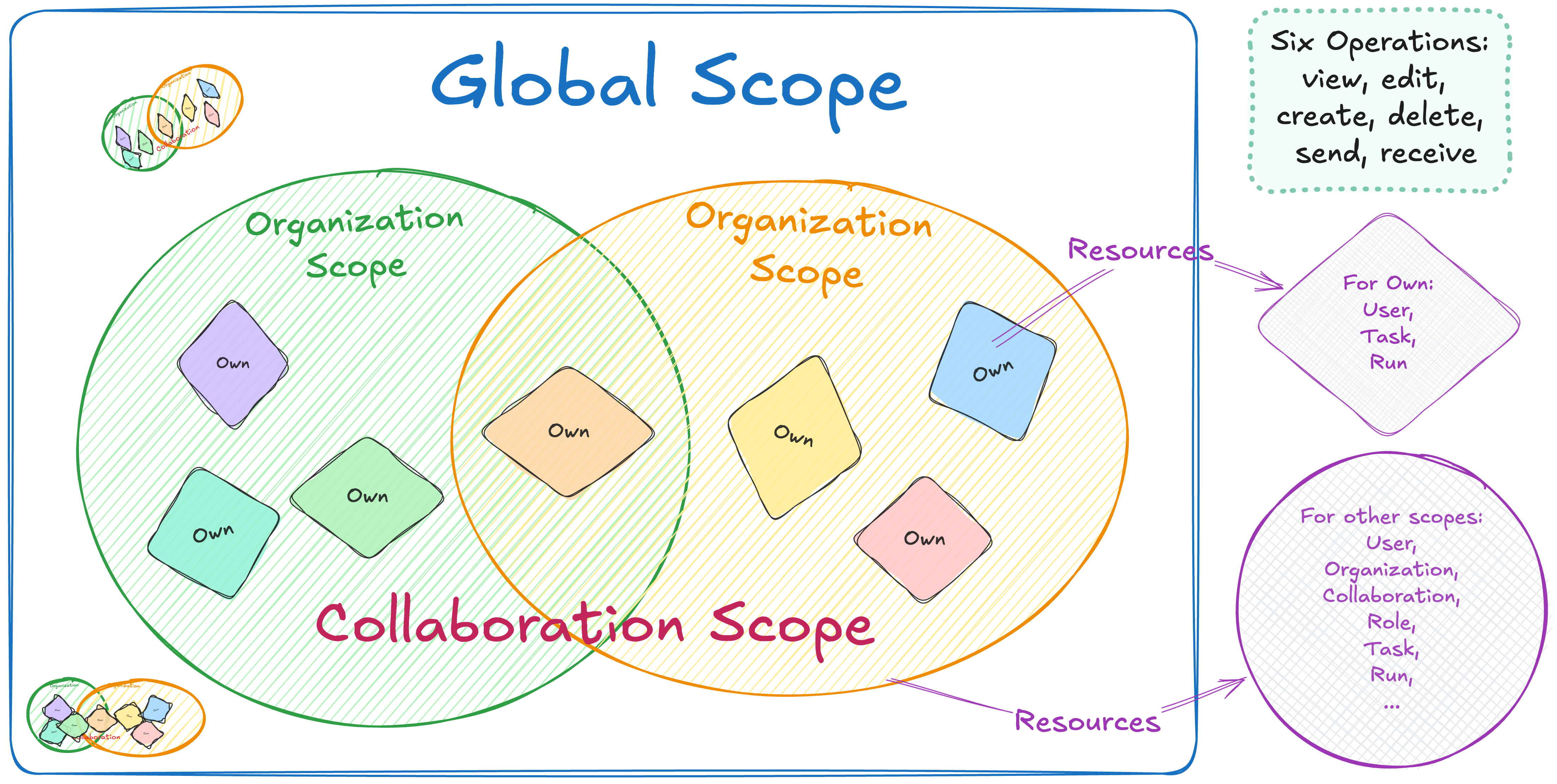
vantage6 permission system
Figure 2
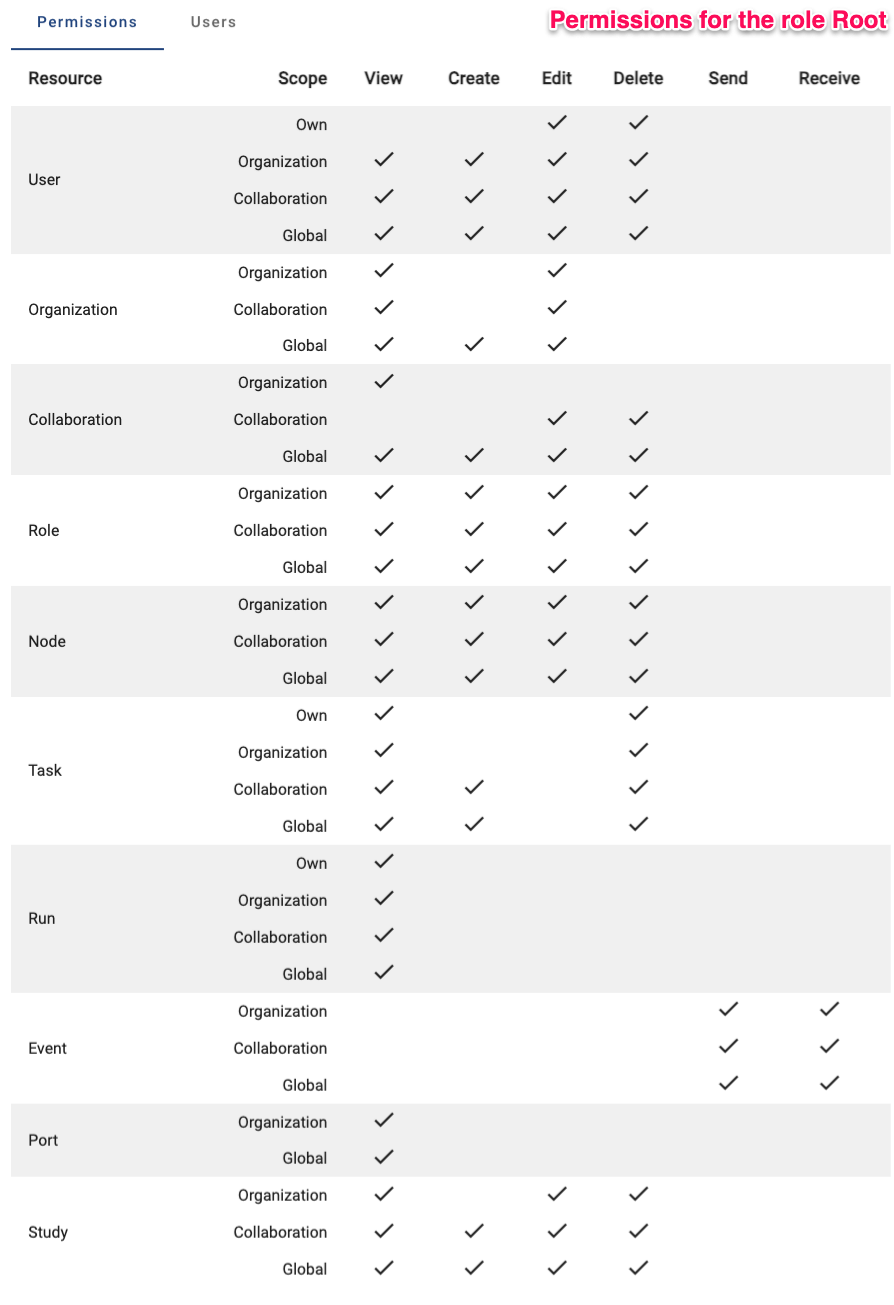
vantage6 permissions for the role Root
Figure 3
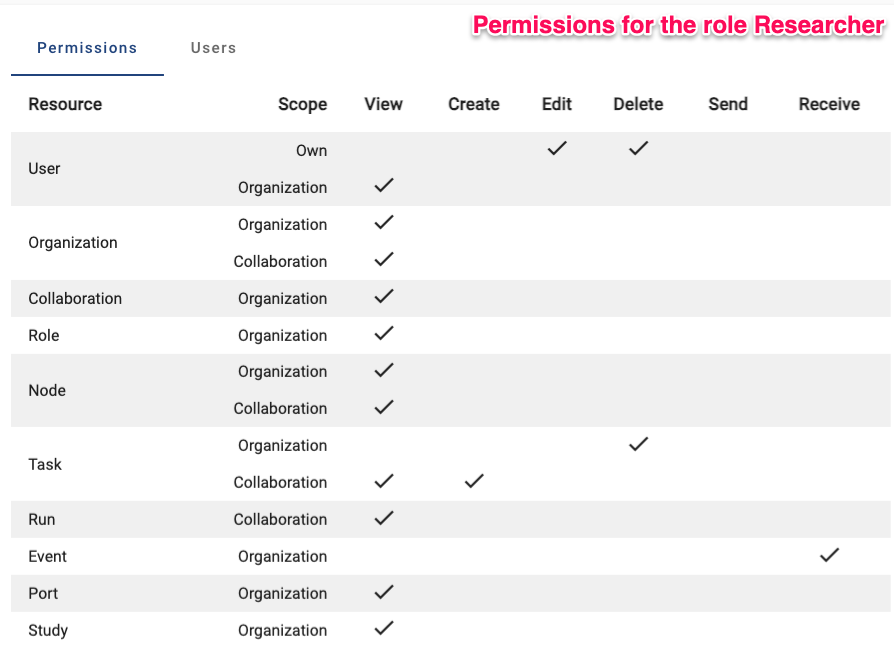
vantage6 permissions for the role
Researcher
Figure 4
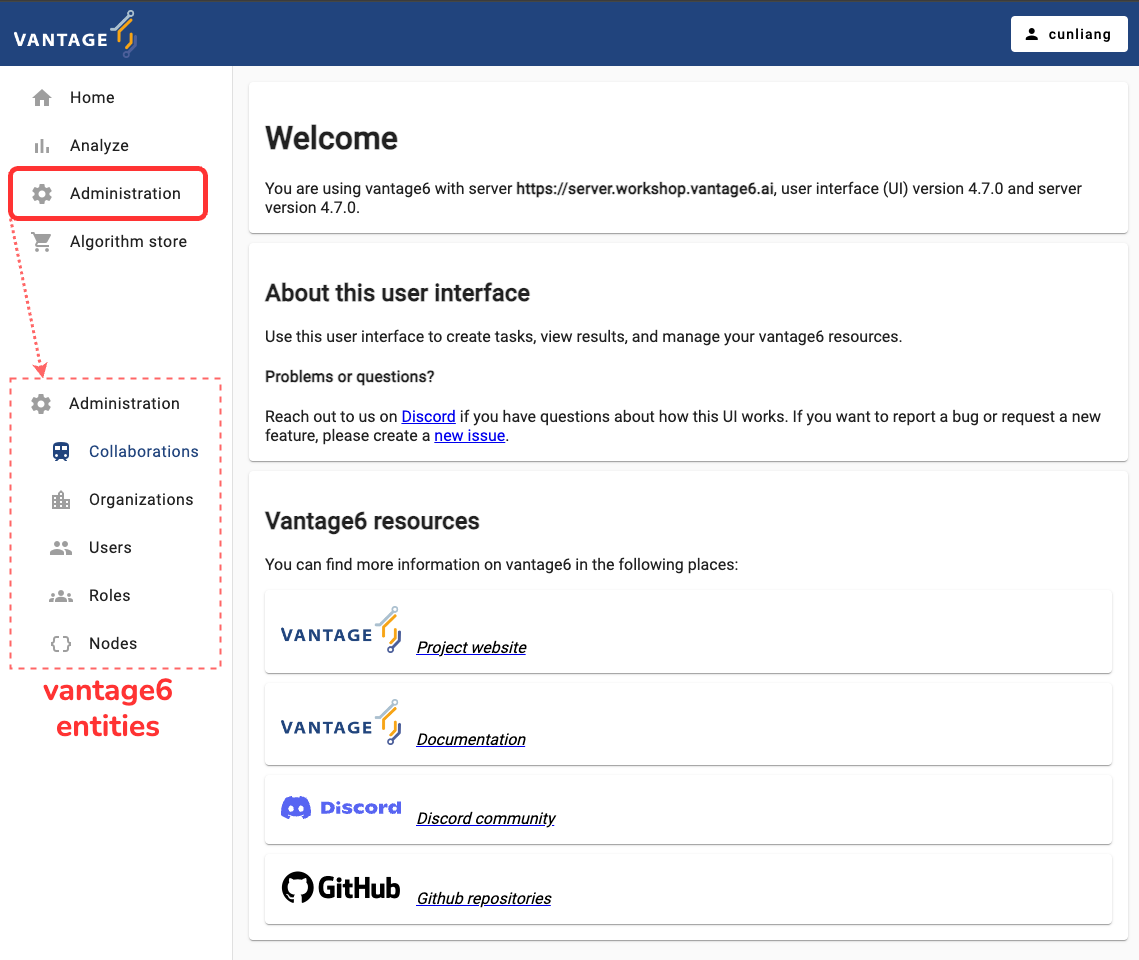
vantage6 UI administration page
Figure 5
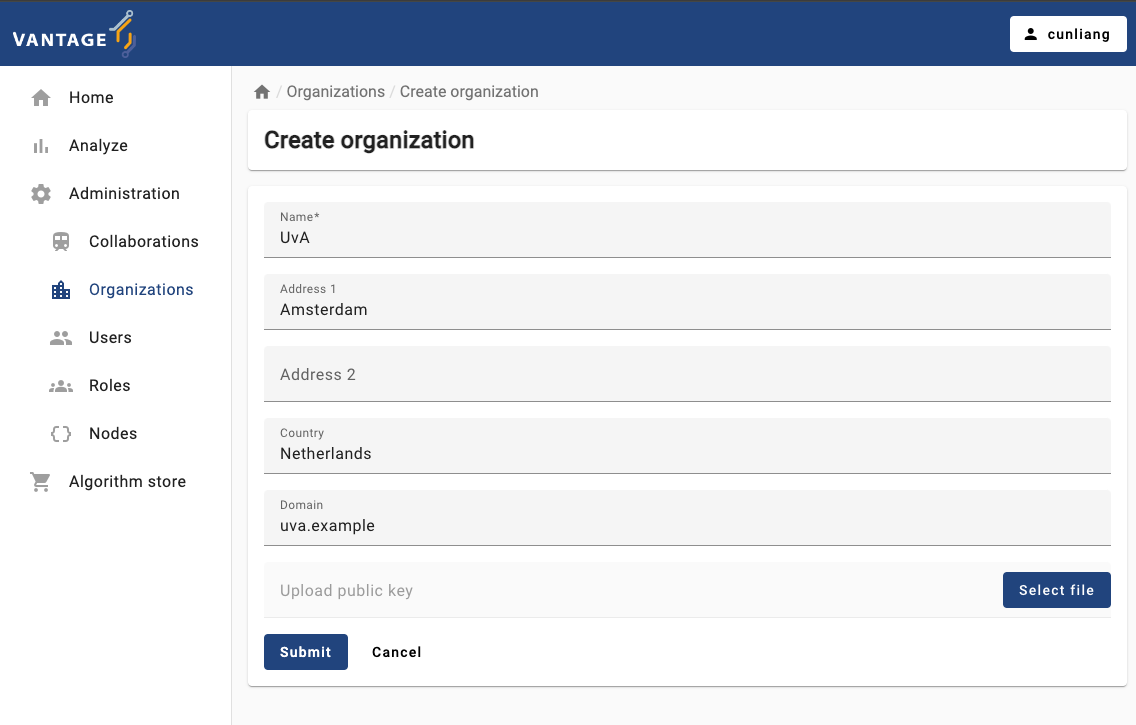
Create a new organization
Figure 6
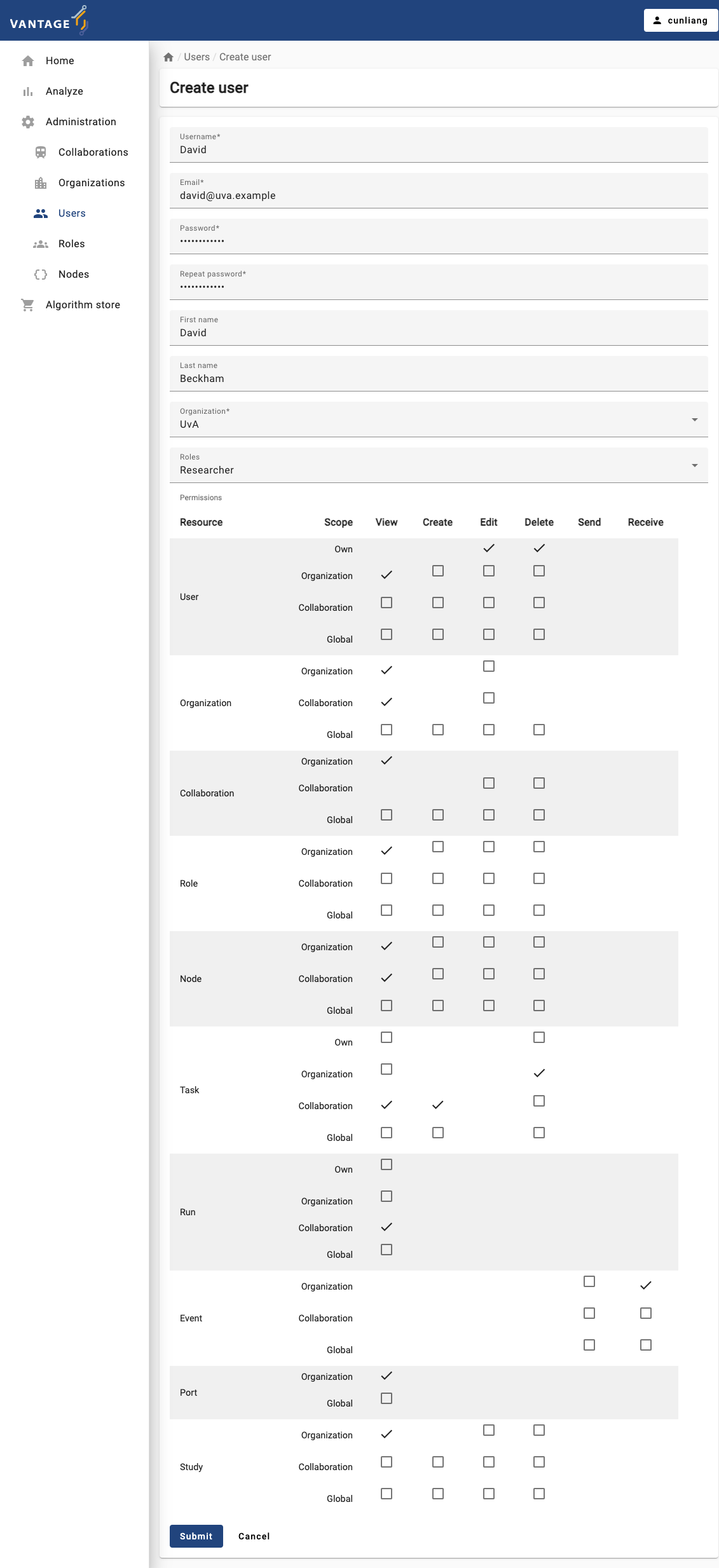
Create a new user
Figure 7
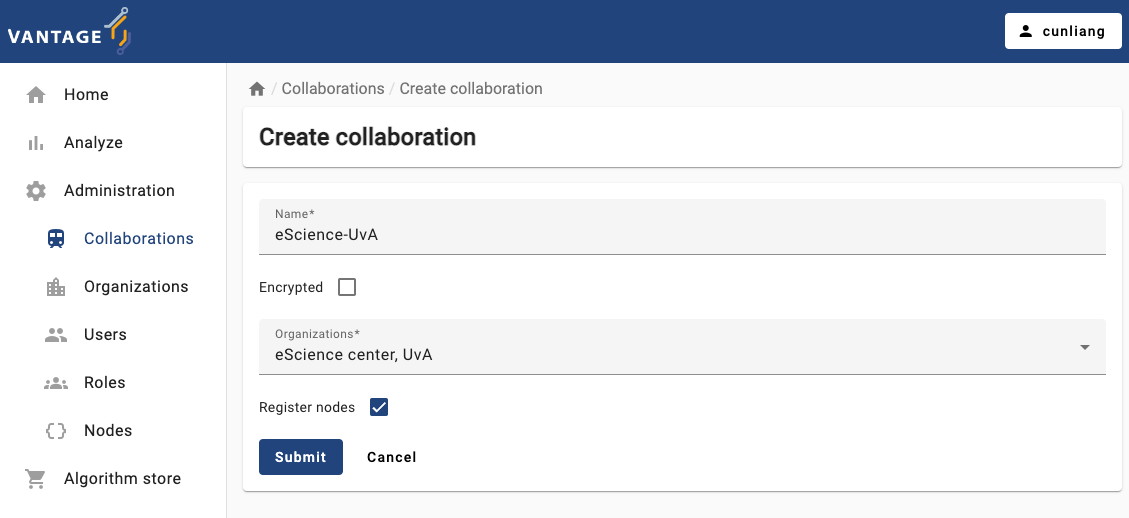
Create a new collaboration
Figure 8
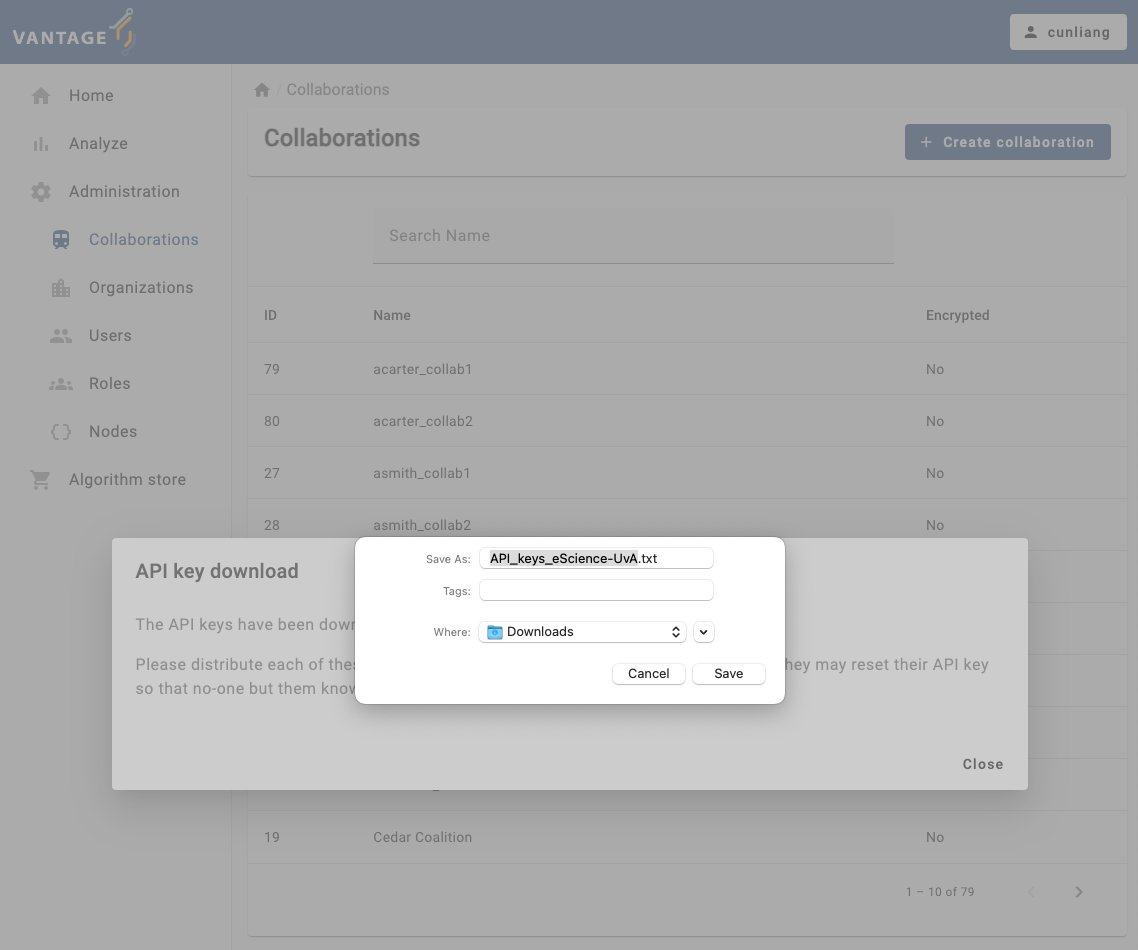
Download API keys
Figure 9
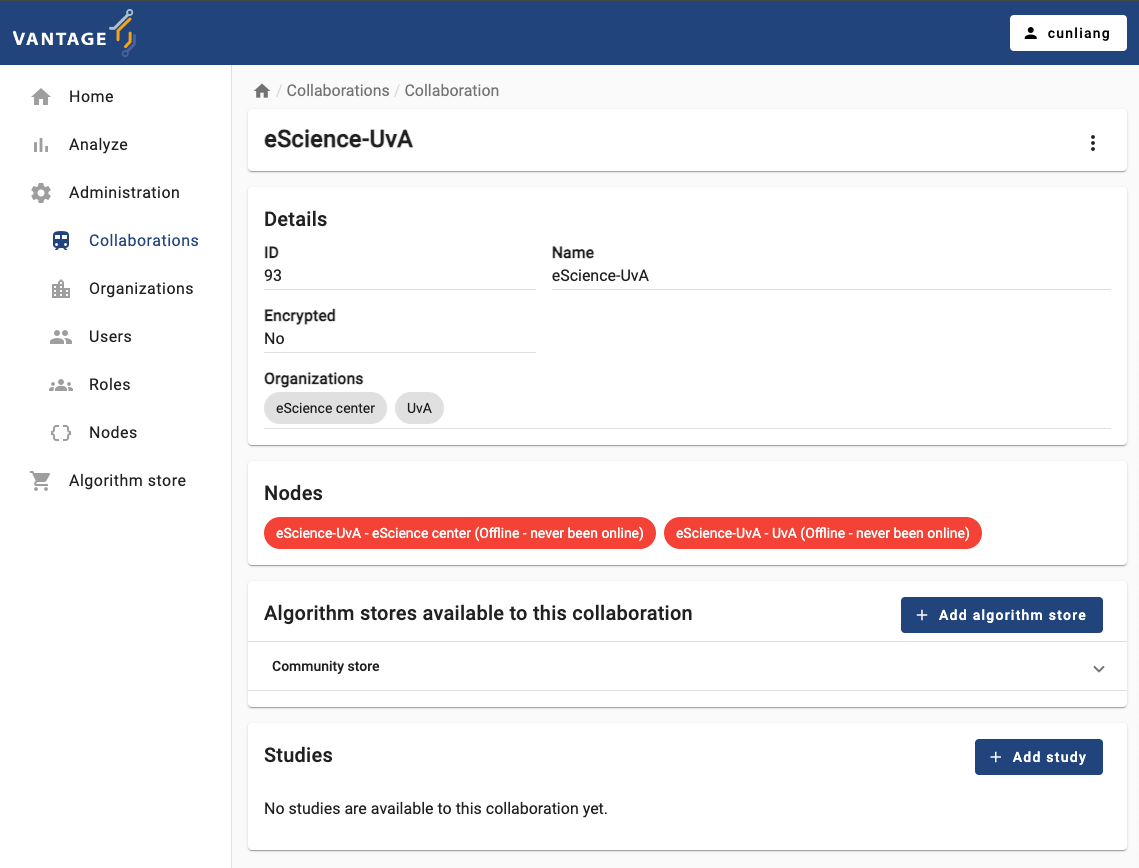
Collaboration details
Running a PET analysis using the Python clientThe Python client
Setting up a vantage6 node
Figure 1
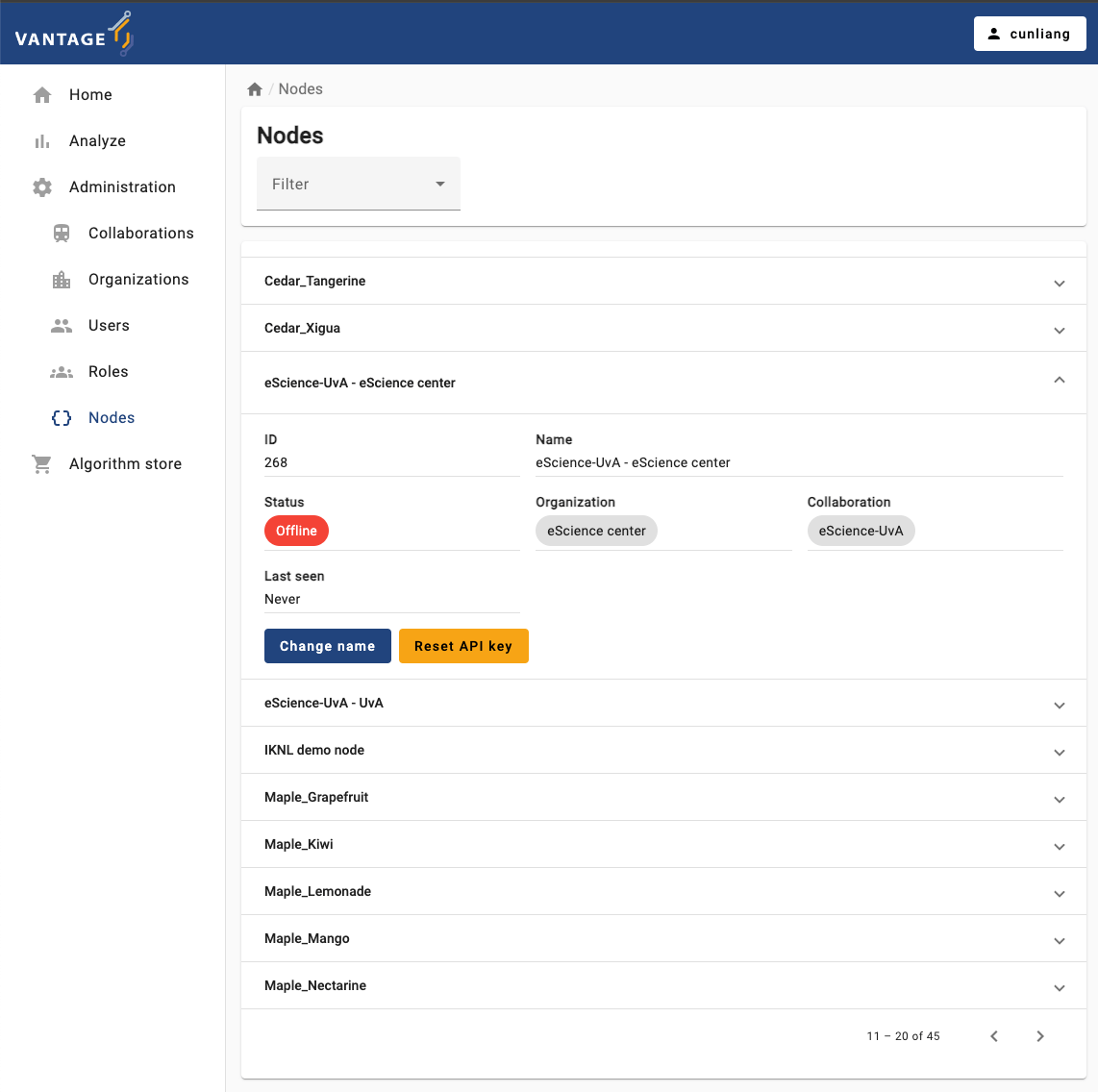
Reset API key for a node
Figure 2
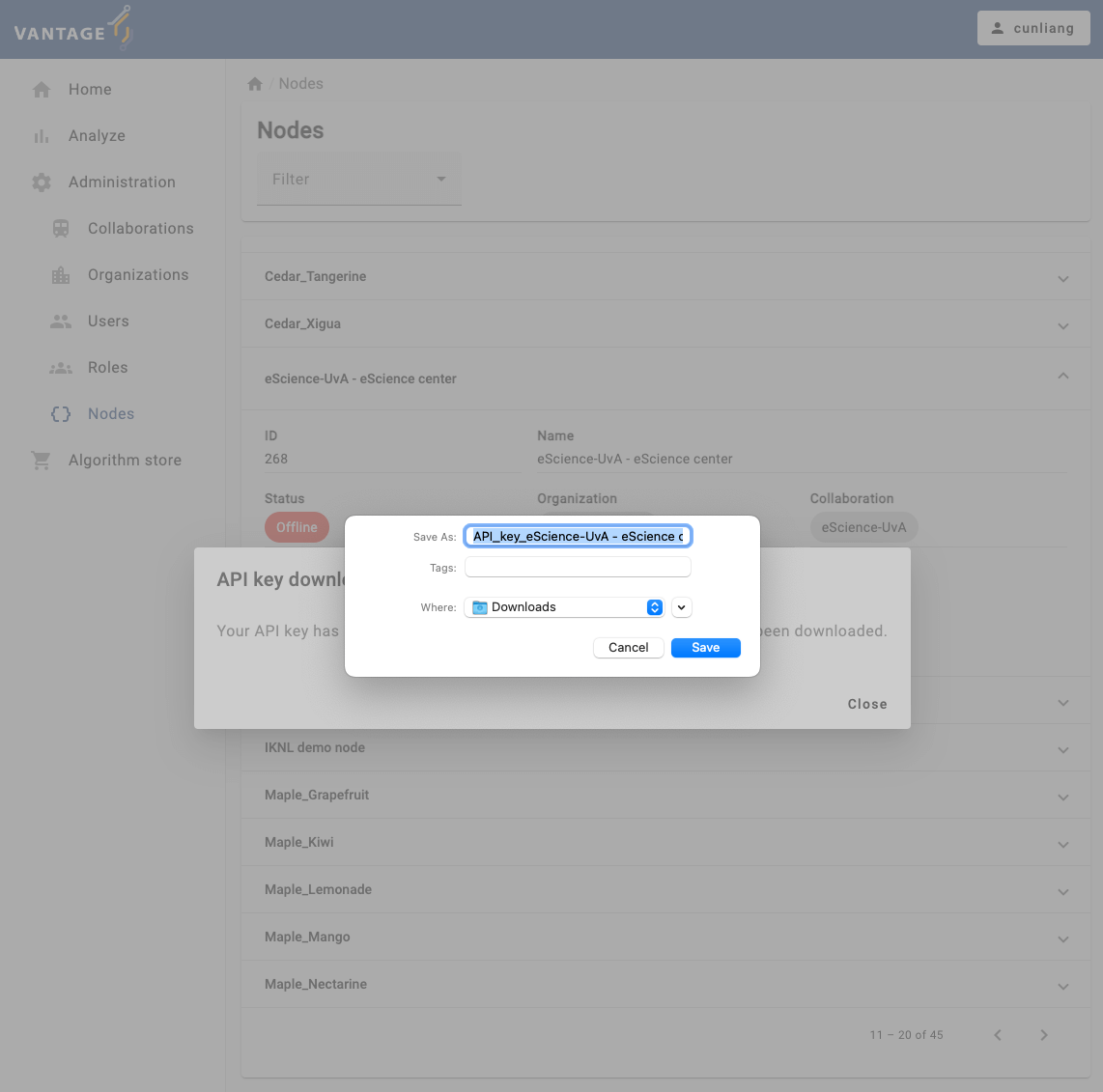
Download new API key
Algorithm development
Figure 1
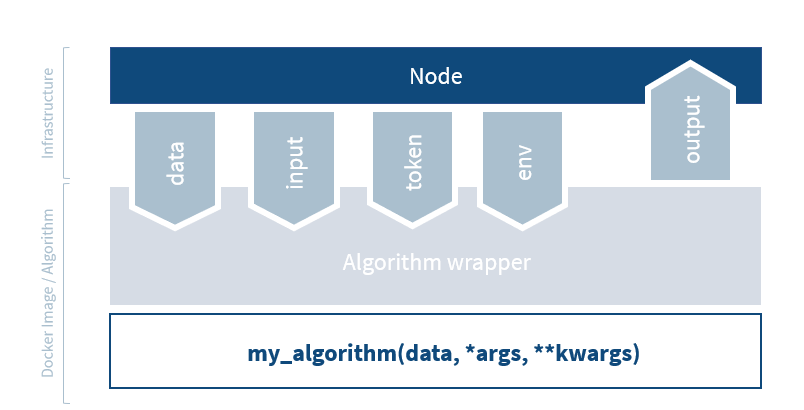
Algorithm wrapper
